How to disable ICMP requests on the PC made with the PING command, in order to hide the computer within a LAN network
 Ping is a command used to check if a particular host (a PC, a router or a site) can be reached through the network; Ping is also used to self-test the computer’s network interface card, or to check the speed.
Ping is a command used to check if a particular host (a PC, a router or a site) can be reached through the network; Ping is also used to self-test the computer’s network interface card, or to check the speed.It works by sending a call request ICMP and send packets with the sole purpose of stimulating the receipt of a reply. Unfortunately, this technique has been used by hackers since the dawn of information technology to verify that the “victim” was online, by pinging the computer to be hit.
READ ALSO -> How to Ping computers or sites and what it means
To try the Ping commandjust go up Start –> runto write cmd and, in the window that opens, write, for example, ping www.How2do.org and, if this site is online, you get a response.
If you go to see the parameters used by the PC to access the Internet, pressing the right mouse button on the two computers (only one in the case of Wireless) located at the bottom right of the screen and choose “State“, we can know the Gateway through which the PC goes out on the network (Press on the tab “Support“).
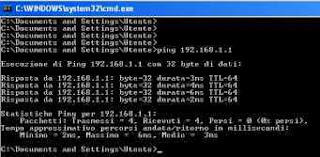
If it is now a little clearer what Ping means, you can understand how it is a very important and fast tool used by network administrators of companies, offices and homes with more than one computer.
At the same time, sending a Ping, is the first weapon used by hackersr to find potential victims on the Internet.
By pinging a specific IP address and receiving a response from that IP address, a hacker can determine that there might be something interesting and unprotected.
Since there are programs that ping entire classes of IPs and can discover all the reachable hosts in a short time, it may be useful, in some cases, to configure your computer to block this answershould increase the level of security for the pc.
You are not anonymous, you do not hide from the network, you simply remain silent to the most common and used type of call, thus giving the impression of not existing.
1) Configurare Windows Firewall
Incoming ping requests can be blocked by enabling simple firewall rules integrated in Windows, without using third-party programs and without having to bother with the command prompt.
To proceed we open the Start menu and search for Windows Defender Firewallopen the corresponding entry, press on the entry Advanced settingsselect the item on the left side Incoming connection rules and identify the following items:
- Basic Network Function Diagnostics – ICMP Echo Request (ICMPv4-In)
- Basic Network Function Diagnostics – ICMP Echo Request (ICMPv6-In)
There are actually 4 similar entries, but we’ll only have to edit those that match the profiles Private; Public (we check the column Profile not to be mistaken).
We open the indicated items one at a time, press on Block the connectionwe tick the item Qualified and press down on OK. From now on, the PC will no longer be able to receive pings.
To learn more, we can read our guide on how configure Firewall in Windows 11 and 10.
2) Use the command prompt
The Ping command can also be disabled from the command prompt, greatly speeding up the process of hiding your PC from hackers.
To proceed, press the Start menu, search cmdright click on Command Promptwe press on Run as administrator and type the following commands:
netsh advFirewall Firewall add rule name="PING IPv4" protocol=icmpv4:8,any dir=in action=block
netsh advFirewall Firewall add rule name="PING IPv6" protocol=icmpv6:8,any dir=in action=block
This command creates two new custom firewall rules to block incoming ping on your PC.
3) Use a router
If we use a router to manage a local network we will be protected from ICMP requests coming from outside the network: in this case, disabling ping on Windows PCs is superfluous, since in fact we will not be able to receive any dangerous ping anyway (unless the hacker connects directly to our network) .
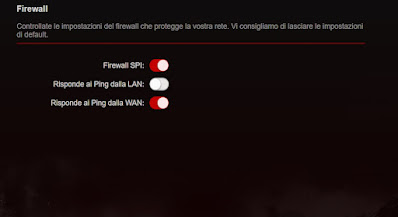
In any case, it is always advisable to check the settings of our router, in order to find out if the ping block or the block to ICMP requests is active, as visible in the image below.
4) Use a third party firewall
If we particularly care about our security and want to effectively hide the PC from hackers, we can block ping requests and any other suspicious connection by pointing to a third party firewalls come ZoneAlarm o TinyWall.
Using these programs we will block ping responses by default, thus preventing hackers from knowing if our PC can be reached on a public network (where we are obviously more exposed to this type of danger).
If we want to try other free firewalls we suggest you read our guide to best free firewalls for windows pc.
If, on the other hand, we often connect to the Internet outside the home, it is advisable to read the safety tips in the articles on how browse safely on public, free or unsecured wifi networks and about how connect to the wifi of hotels, cafes or public networks without internet access problems.
Conclusions
Ping is one of the oldest tools used to check the availability of a PC on a network: many cyber attacks started with a simple “ping”subsequently becoming destructive attacks carried out with other techniques.
Fortunately, nowadays ping has lost much of its “effectiveness”, especially due to the appearance of powerful home routers capable of immediately blocking this type of request.
However, if we do not neglect anything from the point of view of safety or we often surf on public networks it can be a good idea to disable the ping of the computer using the Windows Firewall settings, using the command prompt, or installing a third-party firewall.
To learn more, we can read our guides to Windows 10 and 11 Security Settings and at best free complete and free security and protection suites.
