Guide to try to access a protected wifi network and crack the WPA or WPA2 password using Kali Linux on PC

Obviously we recommend testing these methods only on the networks in our possession or only after asking the owner for explicit consent: we remind you that violating the networks of others without permission is a crime punishable under criminal and civil law, not to mention that nowadays the game is not worth the candle (given the continuous updates and the simple countermeasures that we can adopt to prevent this type of attack).
READ ALSO: Find passwords to access protected WiFi networks
WPS vulnerability

WPS allows you to quickly connect a new wireless device to the modem or router simply by pressing a special button: the connection of the devices is automatic and is based on the exchange of a PIN (generated by the modem or by the router).
Unfortunately this PIN is generated by a very weak algorithm (based on a part of the original modem password and/or its MAC Address): for hackers it was a breeze to create a “copy” of this algorithm and insert it at internal specific programs and apps, so you can “guess” most of the WPS PINs (and reflections of WPA passwords) in modems and modern routers.
So, in fact, WPA2 / AES has not been infringed, but it is possible to access a protected network with this protocol using the WPS vulnerability.
How to break WPS from PC
Download the Kali Linux ISO image and burn it to a DVD or USB stick; in the latter case, we can use Unetbootin to create a Linux USB pen for use on any computer. You don’t need to install Kali on your PC, but only to boot your computer from a DVD or USB stick and then run Kali in Live mode.
Reaver does not, therefore, look for the password by trying thousands of them, it simply bypasses it.
The router PIN, if the WPS connection is active, is eight numbers: The router knows four, while the other devices in which the wifi password is stored know the other four.
A Reaver just tries, randomly, every possible combination of the four numbers until the PIN is caught.
Note: to make this test it is highly recommended to use a laptop with a working Wi-Fi card.
To boot your computer with Kali, we insert the DVD into the drive and boot the computer from the disc or USB stick, as described in our guide on how to start the PC from CD or USB.
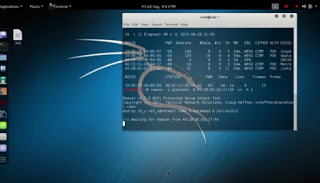
Kali starts with a command prompt: type immediately startx and press Enter to start the operating system interface. In order to use Reaver, it is necessary to get the interface name of the wireless card, the router BSSID you are trying to access (the BSSID is a unique series of letters and numbers that identifies a router)
To be able to crack the network then open the Terminal or Terminal app, then type iwconfig and we press Submit. You should see a wireless device in the called list wlan0 (or even differently).
After retrieving the name of the wireless interface we activate the monitor mode by executing the command: airmon-ng start wlan0 (Assuming the interface name is wlan0); with this command, the interface name in monitor mode will be mon0.
Now we execute the command: airodump-ng wlan0 (Self airodump-ng wlan0 didn’t work, try the command using the monitor interface, then, for example, airodump-ng mon0).
Found the network to be tested, we press Ctrl + C to stop the list e let’s copy the BSSID of the network (it is the series of letters, numbers and two points in the left column).
The network should be WPA or WPA2 in the ENC column.
Now let’s start Reaver by executing the following command in the terminal and replacing the BSSID and the monitor name of the network interface:
reaver -i mon0 -b bssid -vv
For example, it can be reaver -i mon0 -b 8D: AE: 9D: 65: 1F: B2 -vv. After pressing Enter, Reaver will start working trying a set of keys and passwords in a BruteForce attack.
Reaver can put us several hours (even over 4 hours) before pulling out a result that clearly indicates the key WPA PSK.
If the WPA PSK key has been found, we can turn everything off and use one of the tips described in the section on security countermeasures (to be applied as soon as possible).
How to break WPS from Android smartphone
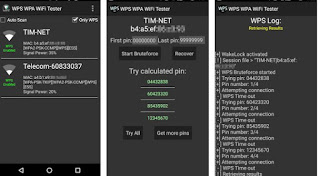
- WiFi Warden
- wifi WPS WPA connect
- WPS WPA WiFi Tester
- WPS WPS WPA TESTER
The effectiveness of these apps is very low, given that nowadays there are few routers and modems in circulation with the WPS vulnerability still active and exploitable (hence the many low ratings within the app). If we really need to test our Wi-Fi network, it is worthwhile to try Kali Linux, which offers more chances of success, leaving these apps only for some tests (just to prevent some children or some Sunday hackers from using them to illegally access our network).
How to protect yourself from the WPS vulnerability
- Disable WPS: this feature is undoubtedly comfortable, but may still be vulnerable on our modem or router. Better then enter the router and disable WPS (usually in the Wi-Fi or Wireless section).
- Change the starting Wi-Fi password: if we change the default password provided by the modem or router, we will make it very difficult to find new vulnerabilities.
- Use the only WPA2 with AES: we ignore all other types of wireless protocol available, namely WPA TKIP, WPA2 TKIP, and WEP.
- Reduce the transmission power of the 2.4 GHz Wi-Fi network: if we live in a small house and are well covered by wireless, we can decrease the transmission power of the modem or router, so as to prevent neighbors or worse anyone steps in the street can stop and use laptops or smartphones to try to access our network, especially if we live on the first or second floor: it is not uncommon to see a good modem covering up to the roadside, also covering areas exposed to risks .
- Switch devices over 5 GHz Wi-Fi networks: if our devices allow it, we always use the 5 GHz network (with IEEE 802.11n or 802.11ac protocol). This network by nature hardly exceeds one or two walls, so it will remain well confined in our house or in our room (also for it the suggestions seen for WPS and password change apply).
To further increase the security of our wireless network, we advise you to read our guide on How to configure the wireless router for a secure Wi-Fi network at home.
Conclusions
In this guide, we have shown you the methods used by hackers, more or less experienced, with which it is possible to crack WPA / WPA2 Wi-Fi network passwords. As we showed you in the penultimate chapter, protecting yourself from this type of attack is quite simple, since the most effective method for cracking such secure networks is the technology that allows you to quickly connect devices (given the danger, better wasting time to enter a password rather than using WPS!).
In another guide, we have shown you other methods for Capture packets and spy on wifi networks. To effectively protect against any hacker threat, we recommend reading our own Online safety guide against hackers, phishing and cybercriminals.
