The security of Microsoft’s cryptographic solution, BitLockersupported directly in Windows, relies on the TPM chip, a component that has become an essential requirement for installing Windows 11. We know that the safest way to date protect data stored on hard disks and SSDs (including system drives) with BitLocker, consists of enabling the use of the TPM chip and the pre-boot PIN request.
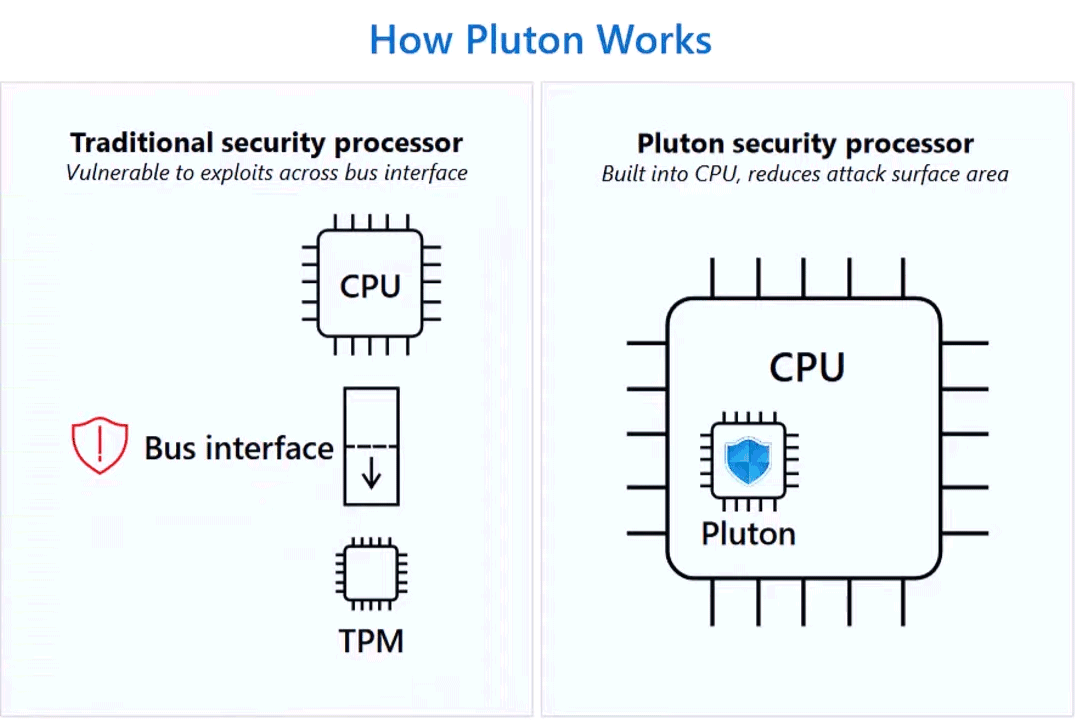
The presence of a dedicated TPM chip on the motherboard and, above all, the pins that allow you to sniffer the data in transit exchanged between the component and the CPU can represent a real security risk, regardless of the bus used. We saw this recently with a series of physical attacks that overcome BitLocker with a logical analyzer or allow you to trace the decoding code with a cheap Rasperry Pi Pico.
Another researcher has demonstrated that BitLocker bypass is possible even on modern PCs, citing examples of notebooks released on the market in 2023 that are equally vulnerable.
In May 2023, there was also talk of faultTPM, an attack that targets the implementation of TPM features at the processor level (fTPM). In this case on AMD systems. The attack in question is not easy to carry out and requires many hours of work but in general, it confirms that the use of the fTPM approach provides a greater level of security. Net of all this, the addition of PIN protection at startup is currently the most effective “shield” that BitLocker users have at their disposal.
Pluton could gain market share on the basis of TPM shortcomings
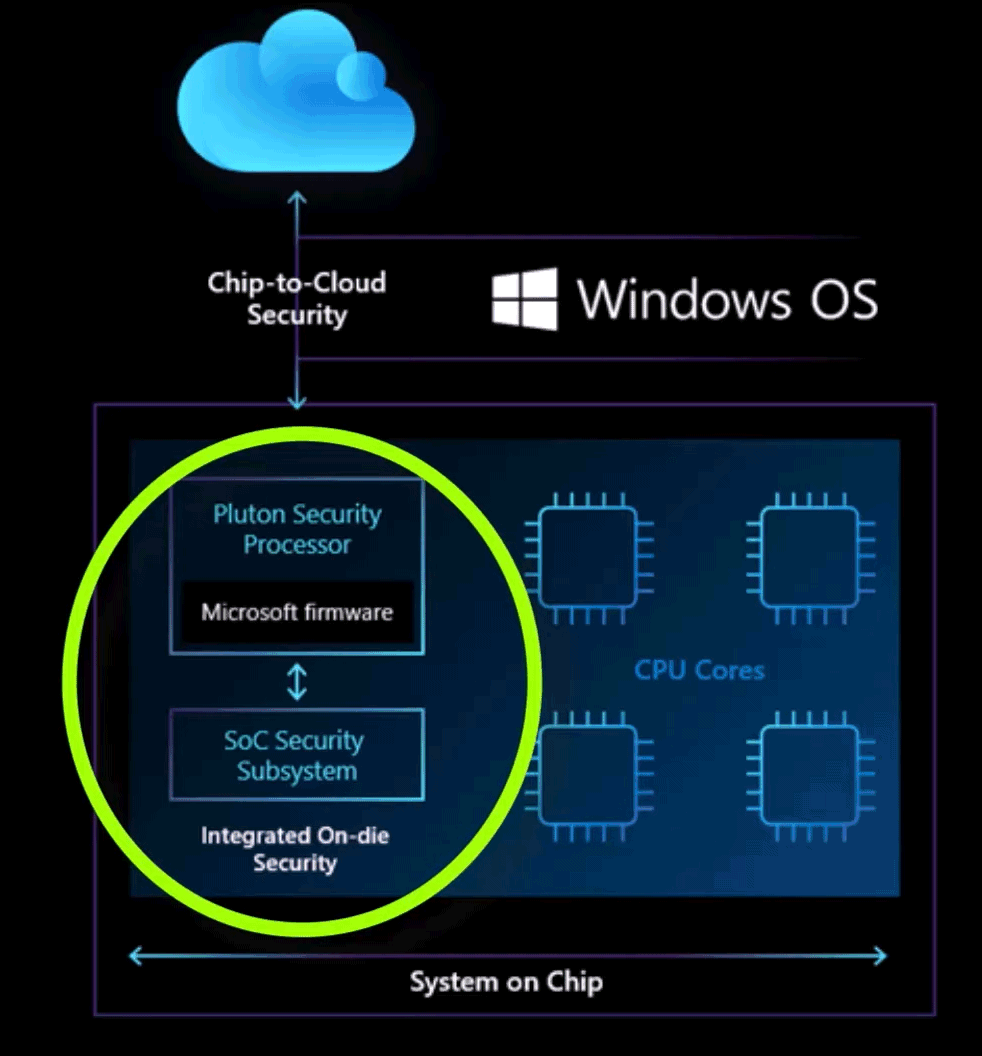
In November 2020, Microsoft announced for the first time Pluton, in collaboration with names such as AMD, Intel, Qualcomm, as well as other “big” names in the industry. Pluton is described as a solution of hardware security integrated and designed to improve the security of Windows devices. The goal is to provide more robust protection against attacks.”man-in-the-middle” (MITM) and hardware interventions.
As we saw in the article dedicated to the first Pluton-based notebooks, the latter is a component integrated into the CPU to provide security features, protect credentials, identities, personal data, certificates and cryptographic keys.
Initially developed for consoles Xbox One and for Amazon SpherePluton is supported by processors AMD Ryzen 6000 (Zen 3+, architecture Rembrandt) and SoCs Qualcomm Snapdragon intended for Windows on ARM systems.
For the rest, the reception – even a few years after its presentation – has remained a bit cold. Intelfor example, while not excluding possible future support from Pluton, he preferred to invest in Platform Trust Technology (PTT). The latter is a security feature developed by Intel that is inspired by the same concepts as TPM and is implemented at the firmware. To the operating system and applications, PTT looks and functions exactly like TPM.
Lenovofor its part, had declared that it would not enable Pluton by default, not even on devices based on Ryzen 6000 and later.
Microsoft recognizes BitLocker’s shortcomings with some TPM configurations and focuses on Pluton
Microsoft obviously supports the concepts behind Pluton with particular enthusiasm, which on the one hand confirms the possibility of overriding BitLocker with specific configurations (recommending the activation of the solution without delay TPM+PIN) but on the other hand invites you to activate Pluton on all hardware platforms if it is already available: “We encourage users who own devices that support Pluton to enable it as the default TPM“.
Microsoft ensures that Pluton is enableable from the UEFI configuration options (Unified Extensible Firmware Interface) for compatible devices and that all instruments that rely on the functionality of the TPM chip are in turn compatible with Pluton.
Disabling the traditional TPM chip before using Pluton
If you are already using BitLocker with a traditional TPM chip, the Redmond company’s engineers suggest you do so disable BitLocker before changing the TPM configuration. After opting to use Pluton from UEFI, you can re-enable BitLocker to associate its cryptographic keys to Pluton. A tool like Windows Hello necessarily needs to be reconfigured after changing the TPM and switching to Pluton. In the case of Windows Hello, Microsoft still recommends configuring alternative access methods before changing the TPM configuration to avoid any access problems.
The same Linus Torvalds decided to integrate support for the TPM CRB (Trusted Platform Module Command Response Buffer) In the kernel Linux in order to embrace the interface that allows, on the software side, to communicate with the Pluton security co-processor.
On the Windows side, Pluton is currently supported in the Pro, Enterprise and Education editions of the Microsoft operating system. As for functionality, Microsoft guarantees full compatibility with Plutonas well as by BitLocker and Windows Hello, also with tools such as Windows Defender System Guard, Windows Defender Application Control, Autopilot, Virtual Smart Card, SecureBIO and the digital certificate management system.
Credit immagine in apertura: Microsoft Bing Image Creator.