USB connections can turn out to be anything but friendly: an attacker can use them to install malware on users’ devices. It is an attack that has been known for some time but which has recently been talked about again. How dangerous is it really? And is it safe to use USB ports for charging smartphones and tablets?
During the Easter holidays 2023, we returned to talk about a long-known cyber attack. Is called juice jacking and refers to the technique whereby an attacker installs malware on someone else’s device using the USB connection.
The expression comes from the combination of two English words: juicemeaning “juice” or “energy”, e jacking which in computer science indicates the action of stealing or taking control of a system. The term is used to simply describe theattack which leverages the connection of the victim’s device to a USB port presented as charging port which instead has been manipulated by the attacker to execute harmful code on the device connected downstream and steal information.
A USB port it can be used both to transfer data and to power the device connected to it, therefore to recharge the battery or simply supply energy.
In theory, the cybercriminal can modify a public chargersuch as those provided in airports, hotels, railway stations, shopping malls and so on, or installing one of its own thus tricking victims into plugging in their personal terminals to recharge its drums. Using a firmware For example, an operating system set up to execute “ad hoc” code when one or more devices are plugged into the USB port, the attacker can cause malicious code to load when the user connects his or her device through the USB cable.
The history of juice jacking attacks
Although there is much talk about juice jacking these days, this type of aggression is well known in the world of cyber security. In 2011, on the occasion of the DefCon of that year, the researchers of Aires Security they set up a demonstration charging kiosk in the area Wall of Sheep of the event demonstrating the practical feasibility of juice jacking attacks.
The screen of the kiosk advertised it as a useful tool for recharging smartphones but when users connected their devices, the display displayed an alert alerting them to the possibility of malicious code execution and the dangers inherent in public charging stations.
A year later, researcher Kyle Osborn described an attack called the Phone to Phone Android Debug Bridge (P2P-ADB) that used the USB OTG functionality: by connecting another Android device via cable to that of the victim, it becomes possible to steal all the data stored inside, including passwords and personal documents. For everything to work, the user must have activated the function Debug USB in the Android Developer Options.
The Android USB Debugging feature is an option that allows programmers to connect an Android device to the computer and run the debugging of android applications directly. When the USB Debugging feature is enabled, the Android device can communicate with the computer via a USB cable, allowing the programmer to test and troubleshoot the application in real time, see system logs, monitor memory usage, and even more. L’enable USB Debugging it is commonly used to proceed with the installation of updated Android ROMs to replace the one already present on the device and no longer supported by the manufacturer.
We returned to talk about juice jacking also during the conference Black Hat 2013 with the presentation of the baptized experiment Mactan by a group of researchers from Georgia Tech. Mactan used electronic components that could be integrated into a wall charger or USB adapter for upload malware on the downstream connected device in just 80 seconds.
In 2015, the researcher Samy Kamkar unveiled KeySweeper, an Arduino-based device that can detect and record all keystrokes pressed with any Microsoft wireless keyboard used within range.
During the DefCon of the following year, the researchers of Aries Security have shown a new attack which consists of carrying out the mirroring of the device to another monitor by launching the concept of video jacking. In this case the USB charging cable recorded and sent the video stream of the victim’s smartphone to a device under the direct control of the attacker.
We have also written several times that it is not safe to connect unknown USB sticks to your PC.
This type of attack has in fact been repeatedly used for attack large companies with cybercriminals leaving abandoned USB sticks in employee parking lots or in areas frequented by staff members. THE USB devices they are in fact among the most dangerous in less traditional cyber attacks but no less effective than the “most popular” ones.
Why do the authorities recommend protecting yourself from the juice jacking attack? How dangerous it really is
Close to Easter 2023, many Europen and foreign online newspapers reported the tweet with which theFBI suggests avoiding using public chargers present in the airportsin hotelin the shopping centers. The suggestion immediately made an echo on a planetary scale.
We press to emphasize that the “exhortation” was published by the FBI offices in Denver (USA) and is linked to a suggestion that the federal police agency has been providing for some time on the Be Cautious When Connected page or “be careful when connected“. Using a tool like Web Archive it can be verified that the same page exists, in the same form and with the same contents, since at least September 2022.
Furthermore, in November 2019, the deputy district attorney of Los Angeles had already issued an alert on the risks of juice jacking during the upcoming holiday season. Since that announcement, however, there have been no cases of harmful kiosks found in public or incidents highlighting the use of criminal practices. For these reasons, at the time many pointed the finger at the deputy prosecutor’s decision, speaking of an “unjustified alarm”.
The FCC also refers to the dangers of public USB charging stations and provides some advice to defend yourself.
When there are upcoming holidays and close to the summer holidays, however, people talk very often about juice jacking even if, in practice, the cases detected over the years are non-existent and do not seem to concern the public charging stations.
In fact, most security experts point out that all the news regarding the practice of juice jacking today comes from ethical hackers demonstrating how code works proof-of-concept. There are no known cases of juice jacking in the “real world”.
Also, modern smartphones notify users when the device is set for data transfer and the USB connection is not limited to battery charging only.
How to defend yourself against juice jacking attacks
Despite the sensational tone used by many media outlets, juice jacking is currently a theoretical attack that is hard to find “in the wild”. However, it must be remembered that a threat is theoretical until it is no longer so: by the time an attack is detected in the real world it is already too late because, evidently, the data has already been stolen.
Dealing with the juice jacking issue properly is the best way to protect data and strictly personal information that we all keep on our mobile devices. Before rushing to connect your smartphone to another user’s device or to one public USB charging socket however, it is good to reflect for a moment.
When the smartphone is connected via cable to the USB port on desktop and laptop PCs the option to transfer files from one device to another also appears. The USB port, we know, is not simply a means of recharging the battery but a tool for transfer data: we saw it, for example, in the article on the differences between USB ports and cables.
A normal USB connector it has five pins of which one is required to power the downstream device: by default, two of the other pins are used for data transfer purposes.
Unless the user has changed the default settings of the operating system, it is on iOS what up Android USB data transfer mode is disabled, except on very old Android devices. In these cases the juice jacking attack cannot initiate because the data transfer is blocked via software.
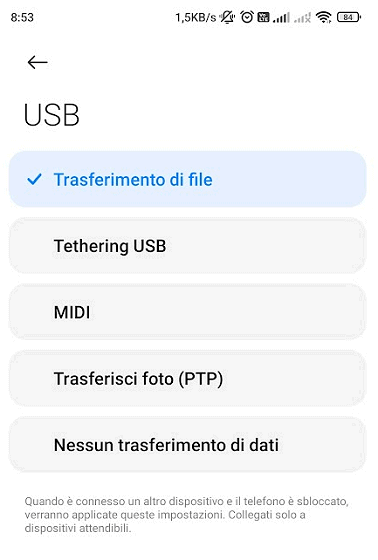
Not only. The latest versions of Android, regardless of the option selected, simply activate USB charging only when the device is connected via cable and screen And blocked. In other words, when Android device is not unlocked, no data transfer can happen via USB (additional reason for secure access to the device with a strong PIN, a pattern that is difficult for third-party users to detect, to use fingerprint unlocking,…).
Finally, the option Debug USB which we talked about previously, which is potentially dangerous, always requires confirmation from the user about the “legitimacy” of the system to which the smartphone has been connected via USB cable. Obviously, the appearance of a message referring to the Debug USBupon connecting the phone to a charging station, should immediately raise suspicions.

