Cubbit is a cloud storage platform that allows you to create and manage immutable backups of your data while protecting them from ransomware, other cyber attacks, and any accidents. S3 Object Versioning and Locking: what they are and why they are important to ensure availability, data integrity and compliance with current regulations on data retention.
In today’s increasingly interconnected digital environment, the cyber threats have become a source of serious concern for companies and professionals. Among the various threats, i ransomware they represent one of the most dangerous and insidious forms of cyber-attacks.
Ransomware is malware designed to encrypt valuable data and confidential information of the company or professional. Once the data is encrypted, the attackers demand ransom money to provide the decryption key and allow data recovery. In some cases, the attackers steal the data stored on company servers and threaten to make it public if the requested sum is not paid.
The consequences of a ransomware infection can be devastating for businesses and professionals but, as we have repeatedly pointed out, this is the latest manifestation of a cyber attack that began much earlier. According to the data of IBMIn fact, 95% of cyberattacks are caused by human errors and have to do, for example, with problems arising from configuration errors, inadequate security settings, lack of information and personnel training. The adoption of the best policies of data backupshowever, lets do business-as-usual even in the event of serious incidents involving the information underlying business workflows and processes.
In its definitive guide to protecting against ransomware in 2023, downloadable from the official site, Cubbit cites a survey by Veeam that found 85% of the companies surveyed last year were attacked by this type of threat. L’EuropeIt also ranks first overall for ransomware attacks second Trend Micro with 75% of companies facing an attack by 2025 (Gartner).
Other data shared as a result of various research on the ransomware phenomenon are certainly no more reassuring: 71% of victims of ransomware lose their data forever (Kaspersky), repairing the damage costs three times the ransom demanded by cybercriminals (Sophos), whoever pays the ransom demanded by a ransomware funds 9 more attacks (Trend Micro) and, above all, 90% of aggressions target their own backup archives (Veeam Ransomware Trends Report) confirming that careful management of backup copies is essential to avoid unpleasant situations in which malware manages to remove the backup information.
Cubbit: complete, effective, safe, modern and economical solution to protect yourself from ransomware and from any incident
The predominant approach to defend against cyber threats and protect data was to use infrastructure on-premises, which require significant investments in hardware, physical space and maintenance. The advent of innovative solutions such as Cubbit opens up new possibilities and introduces advantages significant, especially in terms of safety and cost.
Cubbit offers an alternative approach on-premisesallowing for store and manage data safely and efficiently. One of the main differences compared to the solutions most popular among professionals and businesses until recently is that Cubbit uses a geo-distributed storage: Data is split and replicated across multiple devices, providing greater resiliency and protection against data losses.
Another advantage of Cubbit is the scalability: while the solutions on-premises require the purchase of additional hardware to handle the increase in data volume, Cubbit allows you to extend storage space flexibly and without significant additional costs. This is particularly beneficial for any company that faces the common problem of data growth.
Cubbit is a whole reality Europenbased in Bologna, which offers a proven solution against ransomware, malware and, in general, any incident that occurs in the company or office and which could potentially have a negative impact on theintegrity and the data availability.
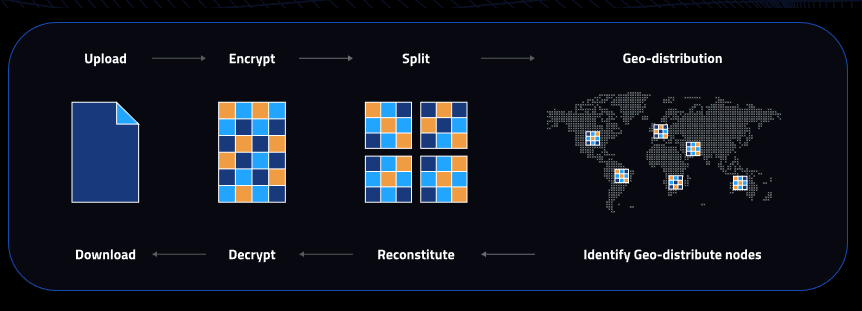
The concept on which Cubbit’s cloud proposal is based consists of data distribution of users on a large number of nodes, geographically separated from each other. The data is encrypted with the algorithm AES-256 preventing its monitoring, analysis, modification and removal by any third party; they are also fragmented into several portions, one indistinguishable from the other. The various portions of the data, called shad (see below), are in turn multiplied into multiple fragments using error-correcting codes Reed-Solomon so you can trust on one redundant scheme e geodistribuito.
To test the service without paying a cent, we suggest visiting the Cubbit home page then clicking on Get started for free per register an account. Cubbit’s cloud storage can be “tested” for 30 days without entering credit card details: you will have them immediately available 30 GB of storage free of charge as well as technical support via email.
Ransomware protection requires proper backup management
In your business or office, an incident involving data availability and integrity is always just around the corner. The key to reacting to any possible problem is to have up-to-date, full backups e consistent.
Lo immutable storage is clearly the best solution to ensure that the data resists the worst case i.e. ransomware infections, the action of malware that damages the contents of files and folders as well as serious accidents that require an effective plan of disaster recovery.
The solution of Object Storage immutable presented by Cubbit is designed to store and manage large volumes of unstructured data. Unlike traditional storage systems, which are organized with a hierarchical file system, Object Storage uses one flat address spacewhich allows you to archive data efficiently and at scale.
In explaining why every business needs object storage, Cubbit highlights how this approach helps mitigate risks associated with ransomware while ensuring data availability and security.
It is also not possible to disregard the adoption of a strategy WORM (Write once, read many) which refers to the ability to write information permanently to a storage device, while preventing its subsequent modification and deletion. The data written to the storage device becomes immutable and can be read many times, but cannot be modified or overwritten, thus avoiding any accidents.
Also for the purposes of data security and integrity, it is also essential to keep a backup copy of one storage offline e air-gappedi.e. disconnected from the network and not accessible through network connections.
It is then essential to use backup with support for the versioning (we’ll talk about it later) so as to keep track of all the changes gradually applied to the company’s files, protect the endpoints and check the backups created on a daily basis: it is useless to arrange for the generation of safety copies if you were not then able to restore them.
Apply the 3-2-1-1-0 backup rule with more than one immutable storage
The traditional approach known as backup 3-2-1 provides for the creation of 3 copies of the data on at least 2 different supports and their storage in an off-site memory location or external to the corporate infrastructure.
The last two numbers “1” and “0” refer, respectively, to the need to store one of the 2 remaining copies in offline mode, using the solution air-gapped or immutable storage as well as daily backup verification.
Cubbit supports the adoption of the backup 3-2-1-1-0 because it contains all the tools for managing immutable backups, securely and outside the enterprise structure.
What are shards in Cubbit
In Cubbit, uno shard it is a critical component of the distributed storage system used to maintain and protect user data. A shard represents a portion of the encrypted data of the user which, as we have previously told, is fragmented and distributed in different storage units within the Cubbit network.
If one of the nodes or disks where a shard is stored should fail, the system is able to generate further copies and thus guarantee redundancy, avoiding any potential information loss.
In addition to the benefits in terms of redundancy and security, shards allow you to easily scale the storage capacities of your Cubbit system.
Cubbit’s geodistributed cloud storage can therefore ensure the highest industry standard of data availability (99.95%): Payload distribution on the network is always automatically optimized ensuring access to data anywhere, anytime.
Versioning and locking: two essential features to protect data from ransomware
Il versioningor the creation and subsequent storage of multiple copies of the various data versions, plays a fundamental role in the fight against ransomware and is also very useful for managing any human errors, such as applying unwanted changes to the file content.
When a system is affected by a ransomware attack and your files are encrypted, you can use backup copies of previous versions to restore the data. Likewise, data versioning offers additional protection against accidental corruptions or human errors. If your data is corrupted or deleted by mistake, you can recover previous versions of files to restore a previous version of files.
Thanks to versioning it is also possible to precisely identify the time when an accident occurred (ransomware infection or any other situation that has endangered corporate data): it can be useful to identify the source of the attack and take effective measures in order to prevent further problems.
Cubbit talks about S3 Object Versioning to describe his service of versioning of objects uploaded to the cloud: S3 is short for Simple Storage Serviceterm used on the AWS service (Amazon Web Services). Cubbit has chosen the same nomenclature to emphasize that its distributed archiving system is fully compatible with the AWS S3 interface: this means that Cubbit users can use their existing applications or services that support S3 to access and manage the archived data in the Cubbit network.
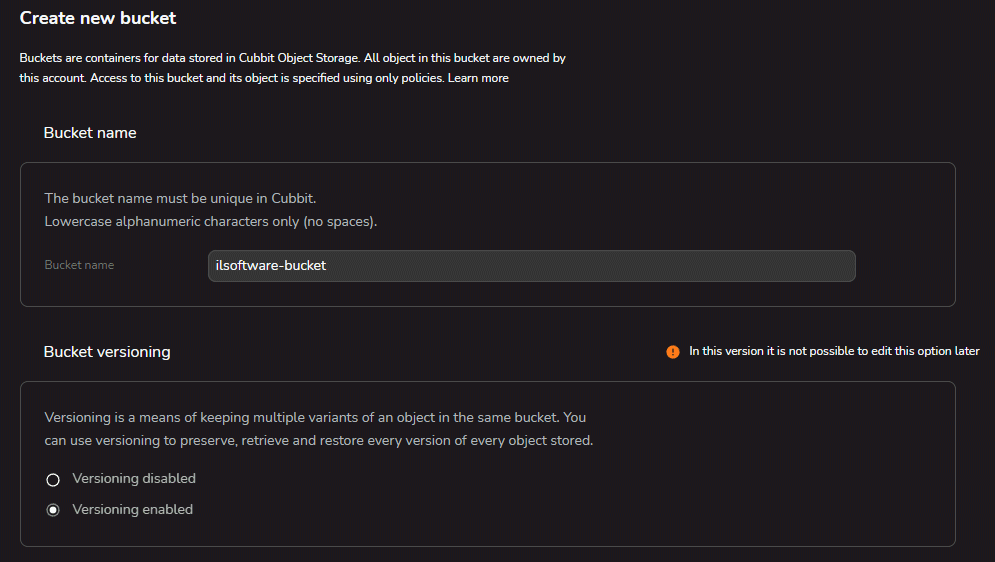
Is called bucket the “container” within which Cubbit allows you to safely save and keep company data: at the time of creation, versioning can be activated simply by selecting the option Versioning enabled.
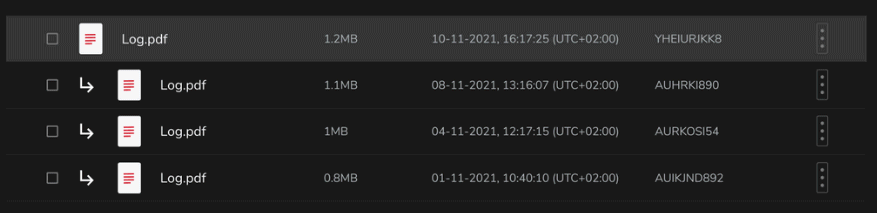
Instead of overwriting your data, Cubbit cloud storage keeps a history of all your items – just click Show versions to access the whole backup history: you can keep, recover and restore each version…