When you purchase remote access software for your company, to work from home (smart working), or to provide remote support and remote assistance for your customers, it is essential to rely on a solution that guarantees the maximum possible security.
The continuous increase in cyber attacks shows a constantly and rapidly evolving threat scenario. These attacks focus not only on individual users but also on the cloud infrastructures behind the operation of multiple services. In the past there have also been major attacks against IT companies that were in fact MSPs that managed thousands of customers (see the case SolarWinds), a factor that impressively multiplies the impact on companies and strategic infrastructures.
Remote Desktop software certainly deserves particular attention from IT security experts, given that by definition they are tools that allow remote access to systems, giving full control over them to those who use them.
Secure Remote Desktop sessions for IT companies
When customers rely on an IT company for remote technical support, especially for servers and critical infrastructures, they want to be sure that the software tools used guarantee the maximum level of security.
Iperius Remote is one of the best software for remote control of PCs and Servers. A great alternative to AnyDesk and Teamviewer, with all the security requirements needed to be compliant with the recent HIPAA and GDPR regulations.
Iperius Remote is multi-platform and works on Windows, MAC and on mobile devices iOS e Android.
Download Iperius Remote Free for free Remote Desktop
We will focus this article on some essential points that peculiarly characterize the security of Iperius Remote:
- 2FA: Two-factor authentication
- Crittografia end-to-end
- TLS 1.3
- Automatic screen lock
- ISO 27001 certified cloud infrastructure
- Multi level password
- Granular permissions
2FA: Two-factor authentication
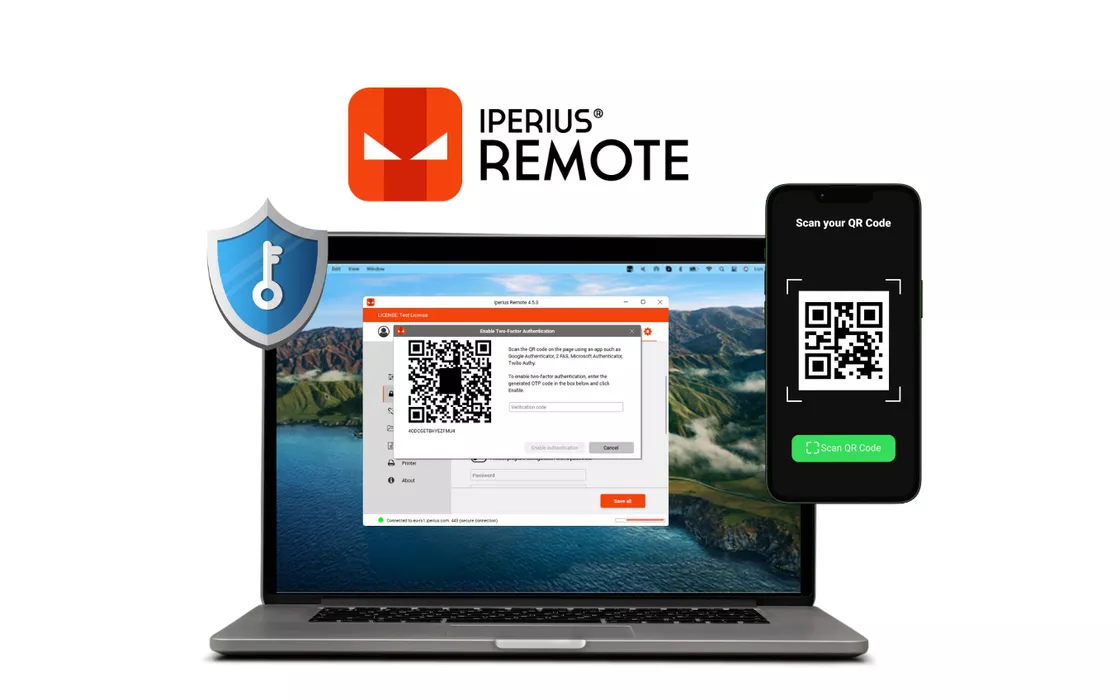
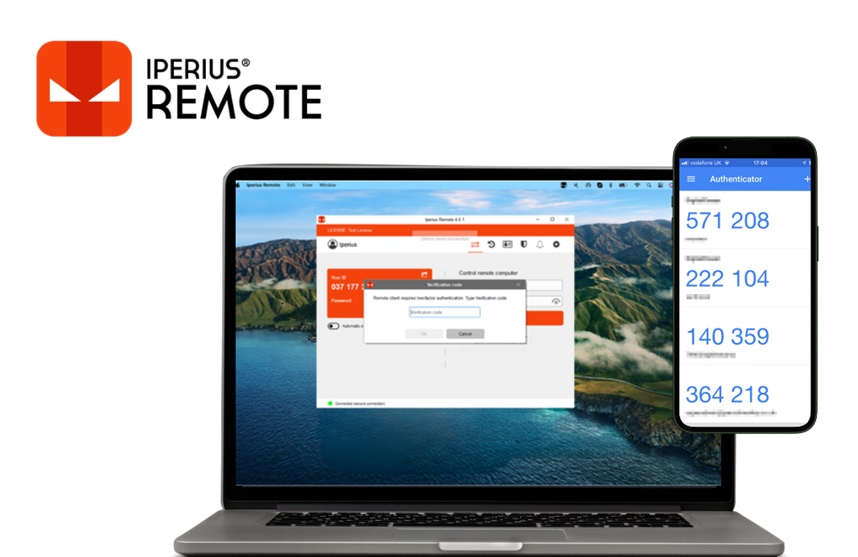
The most secure way to protect a remote computer is to use two-factor authentication (2FA). In simple terms, this means that anyone who wants to connect to that computer will necessarily have to generate an OTP from an authorized mobile device, thus preventing any access that has not passed through this additional authentication layer, even if for some reason a malicious user had come into possession of the ID and password of the remote computer.
How do you set up two-factor authentication? With Iperius Remote it’s very easy. Once the program is open on the remote machine to be protected, we go to the security options and enable the option for 2FA. We will be shown a QR code that we can scan with a special authentication app such as Google Authenticator or other compatible app, via our mobile device. Once this is done, we close the window with the QR code. From this moment on, every time you try to connect to that remote computer, you will be asked forOTP randomly generated each time by the authenticator app.
Here we reach the maximum level of security to access our personal or work computer, or to remotely access a company server for maintenance or monitoring.
Crittografia end-to-end
Encryption is the method by which data that is transmitted, for example, in an internet communication or the contents of a file are converted into a format accessible only to authorized users in possession of the appropriate cryptographic key. This is a process that transforms information into a format that prevents anyone without authorization from reading it.
End-to-end encryption (E2EE) is a specific security technique in which data is encrypted at every stage of its transfer from one device to another. The term “end-to-end” indicates that encryption occurs from the beginning to the end of the data path, i.e. from the sending device to the receiving device. For example, in the case of sending an email, the starting point is the sender’s device and the destination is the recipient’s device.
This technique ensures that communication is protected by preventing any third party from accessing the content of messages, both during transfer between one device and another and when the data transits a server. By using the E2EE to send an email or to transmit video information, no one, including the network administrator, Internet Service Provider (ISP), hackers, the government, or even the company that handles the delivery of the email, can read the content of the message or the content of a video broadcast. This is due to the fact that only the recipient has the unique key capable of deciphering the message.
As a clarification, it is important to point out that the operation of end-to-end encryption is based on the use of cryptographic keys, usually a public and private key pair. The public key is used to encrypt the data, while the private key, held securely by the recipient, is used to decrypt the data received. This mechanism ensures that only the devices of the users involved in the communication are able to access the encrypted content, further strengthening the security and privacy of the information transmitted.
Iperius Remote natively implements end-to-end encryption in all video transmissions (remote desktop), file transfers and chat, thus avoiding any possibility of data interception or compromise.
TLS 1.3
TLS 1.3 is the most recent security protocol available and is implemented by Iperius whenever possible, based on the capabilities of the operating systems where the software is run.
What is the difference between TLS 1.3 and TLS 1.2? This protocol, used by HTTPS and other network protocols for encryption, represents the modern evolution of SSL. TLS 1.3 eliminated support for cryptographic features considered less secure and accelerated TLS handshake procedures, among other improvements.
To provide some temporal context, the IETF (Internet Engineering Task Force) released TLS 1.3 in August 2018. The previous version, TLS 1.2, had been standardized ten years earlier, in 2008.
TLS 1.3 is faster and more secure than TLS 1.2 (which still remains a very high security standard). One of the changes contributing to the increased speed of TLS 1.3 is an update in the TLS handshake procedure: Handshakes in TLS 1.3 require only one round trip (or back-and-forth communication) instead of two, shortening the process by a few milliseconds . Additionally, when the client is already connected, the TLS handshake can occur without any round trips, thus speeding up HTTPS connections, reducing latency, and improving the overall user experience.
To add a technical note, it is important to highlight that TLS 1.3 also improves security through the implementation of a more restricted and secure set of encryption algorithms and hash functions, eliminating those considered obsolete or at risk. This choice is intended to simplify security configuration and reduce the risk of misconfigurations that could expose you to vulnerabilities.
Other security measures
All Iperius Remote connections are protected by AES encryption or password hashing and rely on a server infrastructure in certified data centers ISO 27001 and protected from DDoS attacks, to guarantee maximum service reliability.
At the application level we have protection thanks to multi-level password and very useful support features, such as automatic screen lock when a remote desktop session ends. Furthermore, for connections to which the screen simply needs to be shared, Iperius Remote allows you to limit permissionsthat is, to prevent the use of mouse and keyboard, copy and paste and file transfer.
Clearly, Iperius Remote implements extensive functionality logging both at the local client application level and at the server level, to keep track of every action that is performed and every remote desktop session that is established.
Finally, Iperius Remote allows granular setting of permissions via its web administrative interface, where it is possible to configure access and display permissions in the address book for the various computers, in a granular way for operator users and for groups of computers.
The features of Iperius Remote
To conclude, a brief overview of what the operational characteristics of Iperius actually look like…