Is called email spoofing the technique commonly used to send spoofed emails to appear to come from a source other than the real one. Falsify your email address of the sender is trivial and the practice can be exploited for malicious purposes, such as deception, phishing or other cyber attacks. To avoid being fooled, normal users and computer security software can use reliable methods to find out where an email comes from and who really sent it.
SMTP Smuggling: an attack that undermines the functioning of SMTP servers
A group of researchers from SEC Consultalready known for having discovered other weaknesses in the communication protocols we use every day, reported to various vendor multiple zero-day vulnerability in their respective SMTP implementations.
Acronym for Simple Mail Transfer Protocol, SMTP it is the protocol used to send email messages: born in 1981, it is still widely used today. For example, it is necessary to configure the parameters in any email client or, on the server side, for the components that send emails (think of applications such as Sendmail, Postfix, Microsoft Exchange Server, Dovecot, Exim, Qmail and so on).
Experts point out that the problem named SMTP Smuggling it is anything but theoretical: on the contrary, over the last few months it has involved the intervention of all the main providers who have taken action to give their contribution to the resolution.
Fonte dell’immagine: “SMTP Smuggling – Spoofing E-Mails Worldwide” (SEC Consult).
Sending spoofed emails, which appear to be completely legitimate, to and from millions of vulnerable SMTP servers
In short, by exploiting some differences in the management of the SMTP protocol, an attacker can send spoofed emails still managing to pass the SPF checks (Sender Policy Framework). As we saw when we explained why emails go to the spam folder, SPF it is one of the techniques that helps to unmask any forgery by the sender (email spoofing).
The attack SMTP Smuggling in question allowed the sending of forged emails from millions of domains (for example, from accounts like [email protected]) towards millions of receiving SMTP servers (for example those of Amazon, PayPal, eBay as well as many other providers).
SEC Consult explains that the vulnerabilities identified in the SMTP servers of Microsoft and GMX, for example, were promptly corrected but there are many providers worldwide who are still exposed to the technique today SMTP Smuggling. Indeed, all those who use the product in particular Cisco Secure Emailaffected by the problem, are strongly urged to fix their vulnerable configurations as soon as possible.
SPF, DKIM and DMARC
In our other articles we have talked about methods that help verify theauthenticity of the sender and to prevent potential attackers from sending spoofed emails.
SPF is a mechanism of email authentication which allows you to verify the sender by checking the authorized IP addresses via specific SPF/TXT records at the DNS level. For each domain name, the administrator can, for example, establish the authorized IP addresses for email transfer.
The problem with SPF is that it only checks the domain specified in the campo MAIL FROM of the “envelope” containing the email, ignoring the field From of the header, which can have an arbitrary value.
DKIM (DomainKeys Identified Mail) is another authentication mechanism that allows you to sign message data, including the header From. The signature can be verified by the recipient via a public key present in the DNS.
In the end, DMARC (Domain-based Message Authentication, Reporting and Conformance) provides “identifier alignment” for SPF and DKIM. The system checks whether the “From” domain of the email is aligned with SPF verifications and/or DKIM signatures. If there is a discrepancy between MAIL FROM and From, the DMARC check fails.
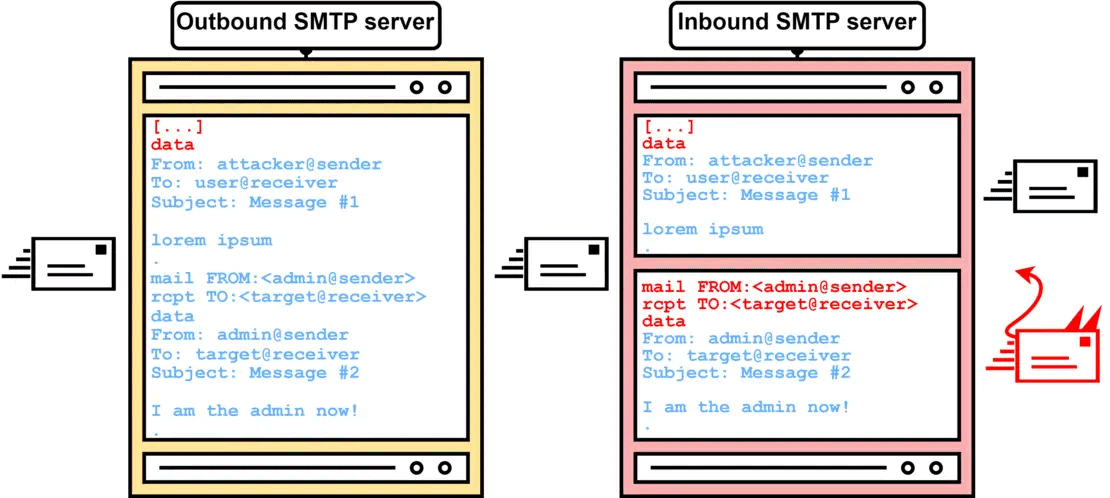
How the SMTP Smuggling attack works
In the context of SMTP, there are two servers involved, the outgoing one and the incoming one. If the two servers interpret the end data sequence (
If SMTP servers interpret differently where the sequence of message data ends, an attacker could potentially extend their action beyond the actual email message data by specifying SMTP commands are considered. The problem could even be exploited to proceed with sending separate emails.
By leveraging the differences in the implementations of the SMTP protocol, and this is the “crux” of the problem, for example by using the sequenza
An incorrect interpretation of the end-of-data sequence can therefore induce the server SMTP vulnerabile to evaluate the following text as commands to be executed, with obvious security risks.
Impact of vulnerability
The technicians of SEC Consult they immediately realized the immense scale of the problem when they found that the vast majority of Internet providers were vulnerable to the problem SMTP Smuggling.
By exploiting a particular data-end sequence, they managed to send spoofed emails from the legitimate domain of the targeted telecommunications provider to other email providers. They demonstrated the ability to send emails spoofate from a domain other than that of the original sender, have identified gaps in multiple software for managing the SMTP protocol.
Highlighting theglobal impact of vulnerabilities, researchers underline the importance of intervening for example on Cisco Secure Emaila solution widely used by various email providers and business email services.
To understand the scope of SMTP Smuggling, just examine its history in the paragraph entitled Timeline: everything started in June 2023 and will end now, at the end of December, with the publication of the technical details.
How to fix the problem with Cisco Secure Email
In the case of Cisco Secure Email (Cloud) Gatewayby default, the configuration “Clean” allows the sending of spoofed emails using
The recommended configuration (Allow) tells Cisco software to forward emails with carriage return characters or line feed directly to the actual email server. The latter, in turn, only interprets the sequence
Opening image credit: iStock.com/Sitthiphong