He teams VMware Threat Analysis Unit (TAU) and in particular the researcher Takahiro Hauryama, have discovered a series of driver Windows vulnerabili whose presence can possibly be exploited by an attacker to acquire system privileges, modify or delete the device firmware, access the kernel and gain full control of the system. The problem is serious because there are many types of Windows drivers affected by the problem, most of which are developed by different manufacturers.
Driver Windows WDM e WDF vulnerabili
From reading the analysis published by Hauryama, it is clear that the vulnerable Windows drivers are of the type Windows Driver Model (WDM) che Windows Driver Framework (WDF). These drivers, used for accessing firmware memory and managing I/O, have serious issues security flaws which allow an attacker to attack another’s machine, even without having particular privileges.
WDM and WDF drivers enable communication and management of hardware devices. They define how devices can exchange data with the Windows operating system and provide an interface between the software and the hardware.
I driver WDM They were introduced with Windows 98 and offer a wide range of features, such as device access, I/O management, communication with the operating system kernel, and other low-level features. THE driver WDF they operate in two main variants: Kernel-Mode Driver Framework (KMDF) e User-Mode Driver Framework (UMDF). They reduce the risk of programming errors and provide a level of abstraction that makes it easier to develop safer and more stable drivers, at least on paper.
VMware TAU has indeed identified well 34 vulnerable driver, of which 30 WDM and 4 WDF. Experts then developed code proof-of-concept (PoC) to demonstrate how such vulnerable drivers could be exploited by attackers.
Beware of vulnerabilities in Windows drivers: almost no manufacturer has fixed the reported problems
Hauryama and his team made it clear that they had reported all the vulnerability to the driver manufacturers but that few companies have so far provided a response. Only two developers (the BIOS manufacturer Phoenix Technologies and AMD), moreover, have taken the security issue to heart and corrected it through the release of specific ones patch.
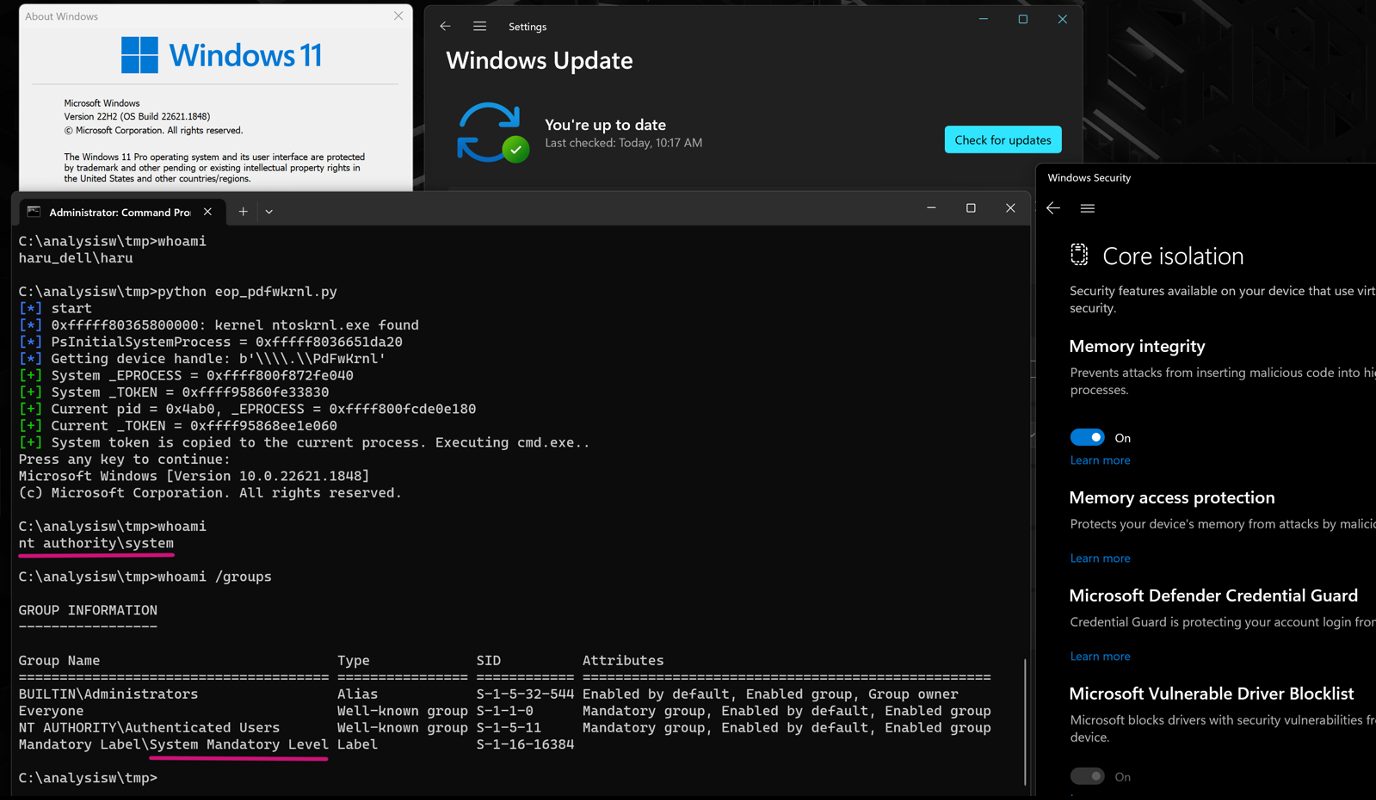
The researchers cite the case of the file as an example PDFKRNL.sys, driver AMD which can be used to execute the command cmdand therefore all the instructions to follow, with the highest privileges ever, even on a system Windows 11 protetto con Hypervisor Enforced Code Integrity (HVCI).
As seen in the image (source: VMware YEAR), by leveraging the security vulnerabilities discovered, a user without rights automatically gains SYSTEM privileges (see the command output whoami). In the analysis you can find the complete list of problematic drivers.
Living Off The Land Drivers: What are
The expression “Living Off The Land Drivers” refers to a category of system drivers used by cyber attackers to exploit vulnerabilities contained therein and gain unauthorized access or elevated privileges. These drivers, considered “legitimate” as part of the operating system or developed by trusted vendors, are often exploited to run malicious activity without arousing suspicion. This is exactly the case of driver Windows vulnerabili discovered by VMware TAU.
The main objective linked to the use of “Living Off The Land Drivers” is to exploit vulnerabilities already present in the system, without the need to introduce new ones malicious codewhich would raise the antennas of the main security solutions.
There is also a site that contains a list of dangerous drivers, which attackers can exploit. For each file the corresponding hash is reported, so that it is possible identify them uniquely.
To combat this type of threat, it is essential to keep operating systems and drivers updated, use effective security solutions and to monitor carefully suspicious activities involving drivers and system processes.
This GitHub repository contains both the script IDAPython to detect any vulnerable drivers and the PoCs developed by the VMware TAU team. The goal is to instill greater awareness in the food industry IT security about vulnerable drivers and the broader problem they represent.