Over time many researchers have tried to overcome the BitLocker encryption using various methods. The methodology just presented in this YouTube video, however, is truly astonishing, at least at first glance (we will make a whole series of clarifications later). Because it allows you to unlock a protected system with BitLocker in a few seconds (43 seconds, to be precise, in the demo shared publicly), “arming” yourself only with a Raspberry Pi Pico card costing a handful of euros.
BitLocker is a cryptographic feature that can also act on entire storage units, such as the system on which Windows is installed. Its main purpose is to protect stored data on hard and removable drives through encryption, for example on Windows 10 and Windows 11.
Some general information on BitLocker
As we know, BitLocker encryption relies on a TPM chip (Trusted Platform Module) to store and manage critical information. In particular TPM allows you to conserve the PCR registers (Platform Configuration Registers), containing information on the configuration of the platform. These logs are used to ensure that the system is booted into a reliable and consistent state before the cryptographic keys are released and the operating system is started.
The TPM chip is also the place that houses the Volume Master Key (VMK), the master key used by BitLocker to encrypt and decrypt the entire storage volume. Everything is fine encrypted volume with BitLocker it has its own unique VMK. Without the VMK it is not possible to decrypt the data and recover it.
Presenting in the past another effective way of bypassing BitLocker (in that case we used a logic analyzer), it emerged that at a certain time the VMK passes in the clear on the bus between TPM chip and CPU. At that moment, therefore, it can be captured and used for decode the data.
How to read the BitLocker encryption key and access protected data
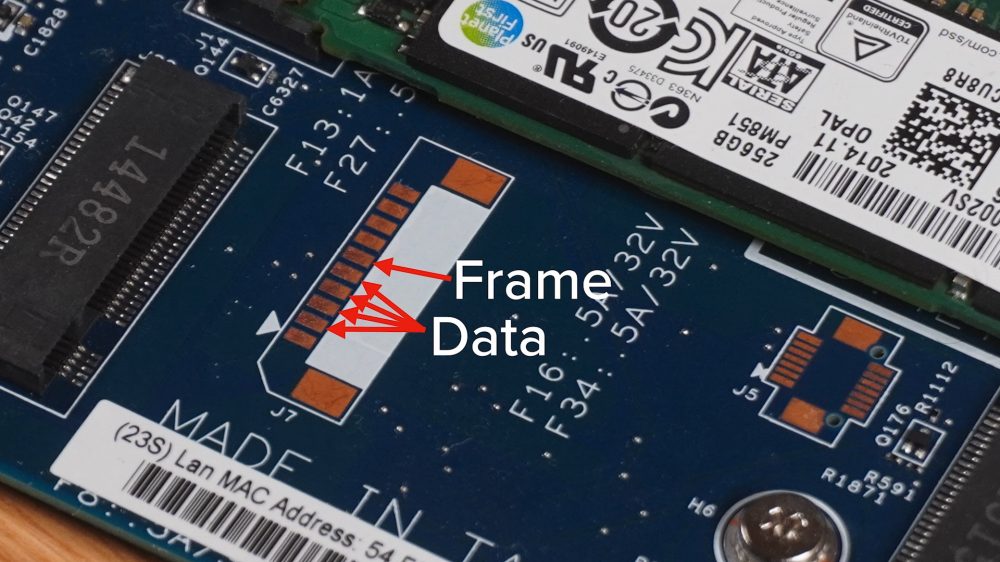
The researcher known on YouTube with the nickname Of stacksmashingcarried out a test its a portable Lenovo branded, 10 years old. He first located an unused connector on the motherboard, near one of the M.2 door of the laptop, verifying how it allowed free access to the data flow on the LPC bus.
Il bus LPC (Low Pin Count) is a low-pin-count communication channel that connects various components of a computer system, including the CPU and devices such as the TPM chip.
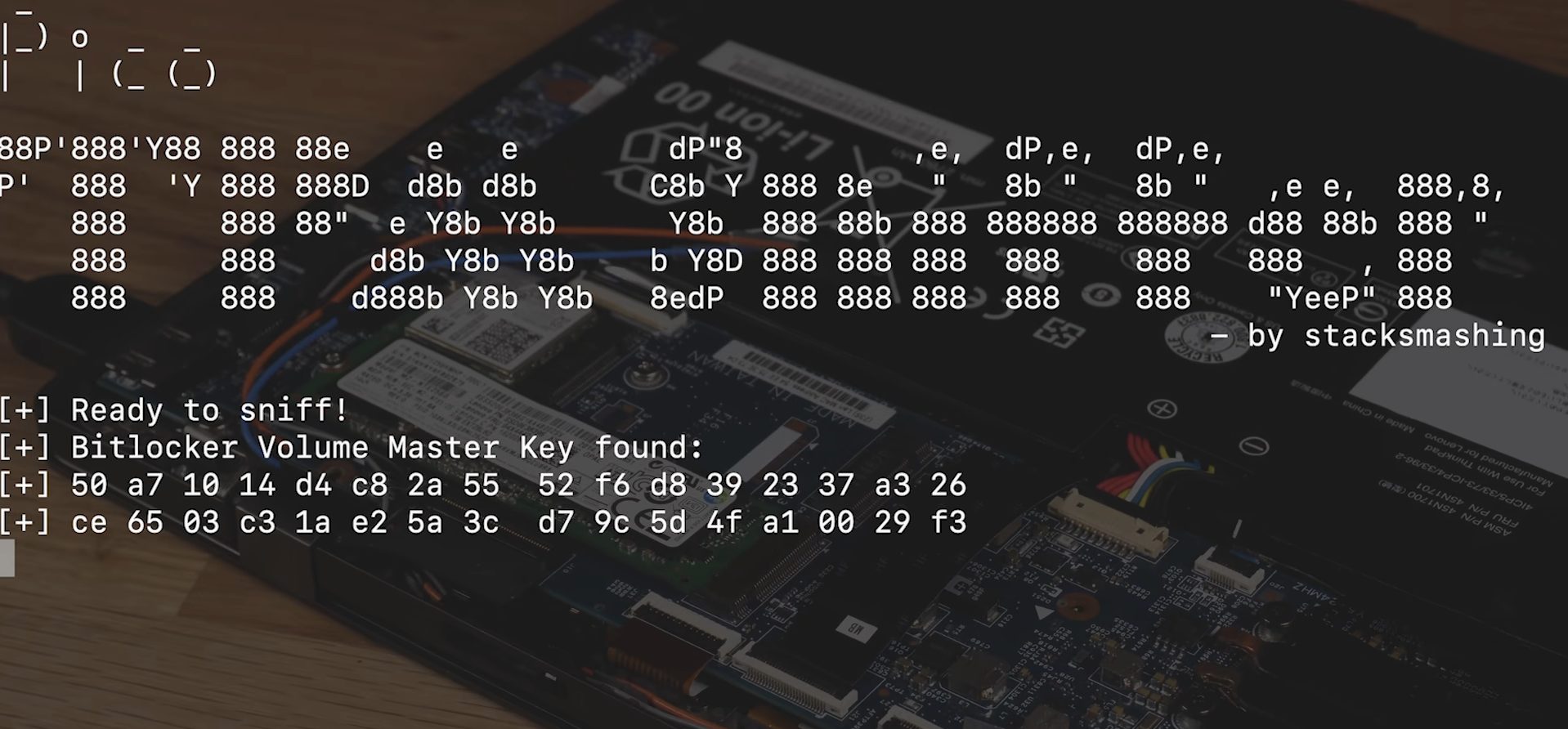
By simply touching the card Raspberry Pi Pico with the connector on the notebook motherboard, the scholar was able to extract the master key (VMK) used by BitLocker to protect data stored on the machine.
The Pi Pico device was obviously programmed in such a way that read the data coming from the TPM chip in format tracks and then expose them clearly to the user. Furthermore, the researcher has adapted the pins on the board so that they fit perfectly with the connector available on the motherboard.
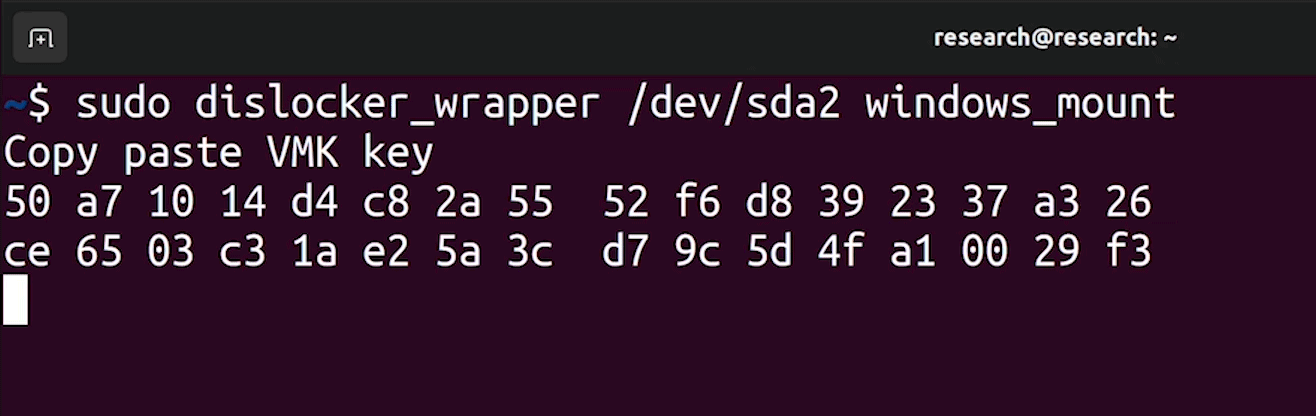
Once you collected the BitLocker VMK key, you simply removed the storage drive (in this case an M.2 SSD), connected it to another system and then used the tool Dislockerto access the contents of the encrypted unit (after entering the master key).
How to defend against BitLocker attacks
We have also observed in the past that the attacks on BitLocker, especially on older systems, are certainly feasible and far from complex. The work carried out by the YouTuber represents further confirmation but does not significantly alter the general picture. Over the years, Microsoft itself has repeatedly had to admit that bypassing BitLocker protection is possible.
As highlighted previously, however, in the video just published online you can see the presence of a connector on the motherboard which provides convenient access to the data processed on the LPC bus. The availability of such a connector was far from uncommon on hardware systems of a few years ago but nowadays it is possible to benefit from defense lines more effective.
The code published by stacksmashing on GitHub, moreover, it refers to the specific case of some Lenovo motherboards, at the moment it only supports the LPC bus but not, for example, communications on bus SPI, which can also be examined with a logic analyzer (as explained in the article proposed at the beginning). LPC is a parallel bus interface with a limited number of pins; while SPI is a more flexible and widely used serial bus interface in more recent times.
Using fTPM
Today, for defend themselves from attacks to BitLocker and make things much more complex for attackers, it makes sense to focus on using fTPM instead of the external TPM chip, for example. fTPMin fact, implements the protection features in the motherboard firmware: therefore, data exchange via the LPC bus which could be intercepted and used for malicious purposes does not occur.
Setting a PIN at system startup
Even more effective, as we have remembered for several years now, is theactivating a pre-boot PIN. Already in 2021 we highlighted that it is possible to hack BitLocker-protected systems that do not use PINs.
It is not possible, and it is absolutely inconsiderate, to rely on a protection model that leverages only the TPM chip: in another article of ours you will find the instructions to protect data with BitLocker by requiring a PIN at startup. Requesting a pre-boot PIN actually adds a additional layer of security to the process of booting and decoding data. Even if an attacker has physical access to the device, without knowing the correct PIN they will not be able to boot the system and access the data. This line of defense is also particularly effective if you remove the hard drive or SSD for use on another system.
The images published in the article are taken from the stacksmashing video. Opening image credit: iStock.com – Orhan Turan