I modern smart doorbells they allow you to see who is in front of your home or office door and give you the opportunity to communicate, even remotely, through the microphone built into the device. There is a wide choice of models on the market but some examples, sold at negligible costs, can constitute a problem in terms of privacy e safety.
Consumer Reports carried out an investigation by checking out some famous ones doorbell intelligent on the market. The conclusions are not positive: according to the technicians who carried out the tests, the doorbells of two Chinese brands (Yes e Tuck) would suffer from some important vulnerability. Among the most obvious security problems, the following have emerged:
- Possibility for an attacker to gain control of the camera of the smart doorbell by placing it in mode pairing.
- Access to thumbnails and “still images” captured by doorbells simply by knowing the device’s serial number.
- Sending via the Internet the public IP address used by the user and the SSID of the WiFi to which the device is connected without use any form of encryption.
Be careful with the smart doorbells you use: those that are excessively cheap can expose you to the risk of attack
As researchers observe Consumer Reports, Eken and Tuck doorbells are currently resold under at least 10 different names. The lowest common denominator, however, is the use of a single application for the cloud management: It’s called Aiwit. Therefore, if you use this application to interact with one or more products, it is a good idea to “straighten your antennas” and consider replacing the product. Unless they are released firmware updates decisive and convincing.
Second Consumer ReportsUnfortunately, the latter scenario is rather unlikely. An email sent to the only address found on Eken’s website bounced back with the classic message Mail Delivery Subsystem Of delivery failure. Additionally, the company’s social media accounts were last updated at least three years ago. A situation that certainly does not bode well.
Some retailers have already made it known that they have withdrawn the smart doorbells in question, following the report Consumer Reports. The detailed report, among other things, highlights that several products lack the FCC registration/authorization code (Federal Communications Commission), which is absolutely unacceptable.
The volume of information accessible without authorization is truly significant
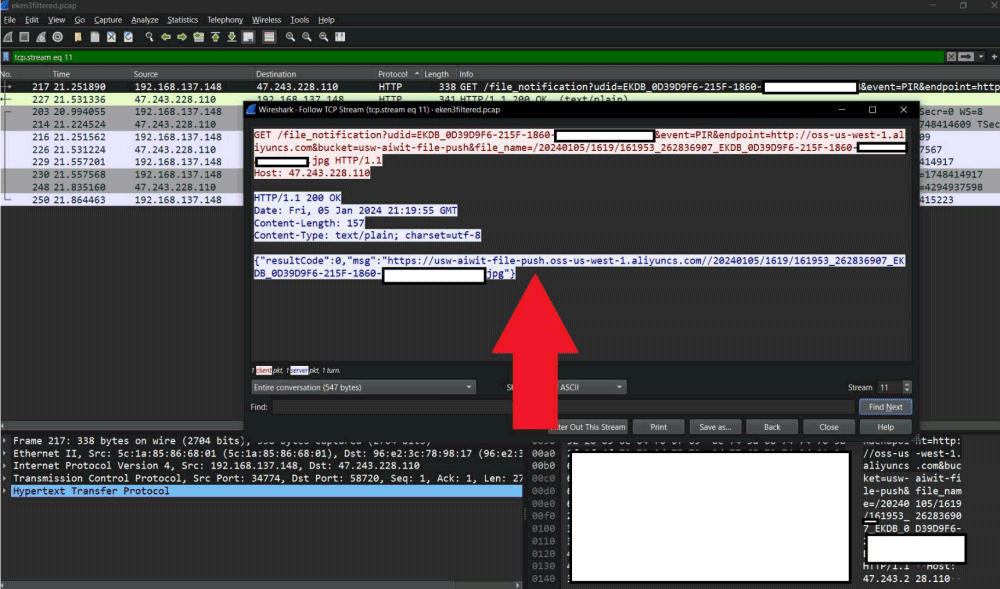
Speaking of technical details, Consumer Reports emphasizes the enormous amount of data (including static images in JPEG format) that these smart doorbells send without using any form of encryption.
Look at the following image (source: Consumer Reports): By using Wireshark to intercept traffic generated by the Aiwit app, it is quite easy to find references to images previously shared by the smart doorbell with remote servers.
Yes, because a possible malicious user can physically stand in front of the doorbell and place the device in the pairing mode (however, it is not possible for all models…) then assume complete control, with the possibility of also verifying the data previously managed. All using the Aiwit app.
The legitimate owner may only notice the problem when receiving an email alert: the communication contains a link to regain control of the doorbell.
An excellent solution is to set up an offline smart home solution that allows you to free yourself from the closed ecosystems of individual producers and avoid always relying on the cloud.
The opening image is taken from the Eken website.