The role of a DHCP server (Dynamic Host Configuration Protocol) is well known: it deals with automatic and dynamic assignment IP addresses and other configuration options to client devices within the network. Akamai explains that 40% of the networks it constantly monitors rely on Microsoft’s DHCP server. Precisely this component, however, suffers from some vulnerability security issues that – reported to Microsoft – the company does not intend to resolve.
Akamai and Microsoft clash over DHCP vulnerabilities
In a long and detailed analysis, Akamai technicians explain that by launching an attack against Active Directory domains that exploit the functionality Microsoft Dynamic Host Configuration Protocol (DHCP), an attacker can spoof important DNS records, with consequences ranging from credential theft to complete compromise of the domain. The attacks do not require knowledge of any credentials and work with the default configuration of Microsoft’s DHCP server.
This alone should make the vast majority of IT administrators perk up. Yet, although Akamai reported his findings to Microsoft, none are currently expected correction.
In the technical text developed by Akamai, the company explains in detail the dynamic update process of the DNS (Dynamic Update) and the role of Microsoft’s DHCP server in this context. In fact, the default configuration of the Microsoft DHCP server enables the “DHCP DNS Dynamic Updates“, which allows the DHCP server to register DNS records on behalf of the client without authentication.
An attack”DHCP DNS spoofing” can therefore allow attackers to forge DNS records that are not defined at the Active Directory level; the second, called “DHCP DNS overwrite“, even allows you to overwrite existing DNS records.
How to avoid attack risks if you use Microsoft DHCP
Akamai experts have put a lot of effort into putting all the risks associated with the use of the software into context as much as possible DHCP DNS Dynamic Updates.
The company refers to two types of records: those created and managed by the DHCP server and records added directly by Windows clients. First of all, to avoid any risk of attack, Akamai advises IT administrators to:
- Disable completely DHCP DNS Dynamic Updates if you do not need this functionality.
- Otherwise, it is advisable to create a user con limited privileges and with a strong password, used exclusively to manage DNS dynamic update operations via DHCP. This is critical if the DHCP server is actually running on a domain controller.
- The so-called Name Protection It’s a feature designed to protect records managed by the DHCP server, but attackers can actually bypass it quite easily. However, it is still recommended to keep it enabled to make unwanted overwrites more complex. Akamai suggests checking that Name Protection is enabled at the scope level for each of the “scope” present on the server.
One “scope” represents a range of available IP addresses that the DHCP server can assign to devices on the network: Akamai explains that the goal is to ensure that the Name Protection is enabled on the various address blocks, helping to mitigate DNS record overwriting attacks associated with the various devices. - The group DNSUpdateProxyagain according to Akamai, should never be used because it represents a security risk: all records created by its members are susceptible to unwanted overwriting.
Microsoft will not fix the issues reported by Akamai
Responding to Akamai’s requests, Microsoft technicians observed that the issues placed on the table correspond to the design by-design and do not require any corrective intervention.
“We tend to disagree. The impact of the attacks we have highlighted can be very significant: the ability to overwrite DNS records without any authentication allows attackers to take advantage of a scheme machine-in-the-middle on the domain hosts“, is observed by Akamai. “This could easily expose sensitive information and personal credentials; could also open to relay attackallowing attackers to hijack Active Directory domains and gain elevated privileges“.
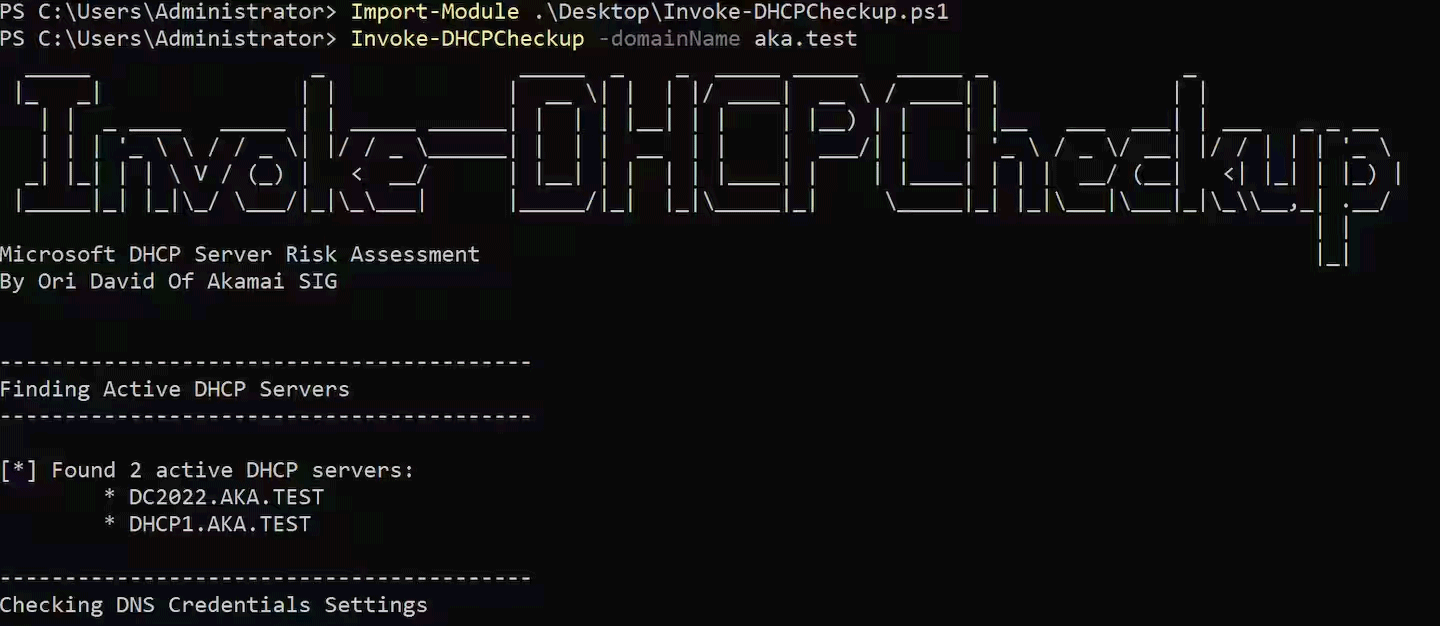
Since there is no solution to the problems discovered by Akamai, the company encourages technical department managers to use the free Invoke-DHCPCheckup tool. This is one script PowerShell developed by Akamai engineers that helps detect and surface misconfigurations of Microsoft DHCP servers.
In any case, anyone who has not changed the default configuration of the service is automatically vulnerable.
Akamai concludes by revealing that it will be releasing soon DDSpoof (DHCP DNS Spoof), a software tool that implements the attacks described in the analysis. The tool clearly shows how unauthenticated attackers can collect data from DHCP servers, locate vulnerable DNS records, overwrite them, and use this ability to compromise Active Directory domains.
It is therefore a head-on clash with Microsoft with a strategy, that of Akamai, which seems clearly aimed at overcoming the inaction that seems to shine through from the responses received through Redmond managers. With the aim of strengthening the configuration of every company that uses Microsoft DHCP.
Opening image credit: iStock.com/Nadezhda Kozhedub