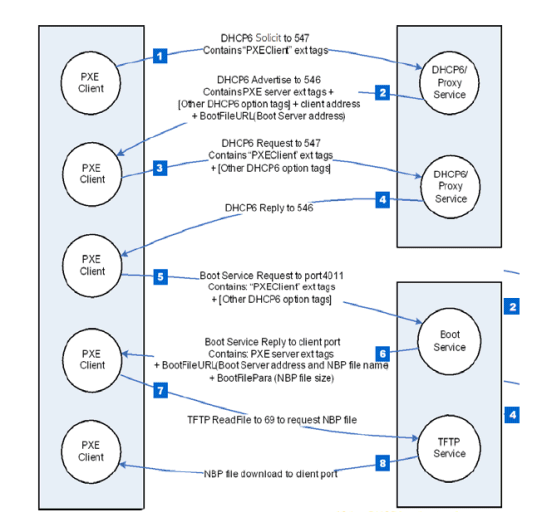
Il boot via PXE (Preboot Execution Environment) is a method that allows a computer to boot and load an operating system from a network resource rather than from a local storage device, such as a hard disk, SSD drive, or external USB storage media. This technology is particularly useful in environments remote management systems, such as data centers or corporate networks, where operating systems need to be installed or updated on multiple machines without having to use physical media.
It doesn’t mean that PXE can’t also be used in the office or in home environments: in the article dedicated to how to install Windows via PXE over the network, we saw that it is necessary to configure a server system in the LAN. The latter contains the resources necessary for startup, such asoperating system image that you want to distribute. The DHCP protocol (Dynamic Host Configuration Protocol) is often used for assign IP addresses and transfer boot information to computers that require PXE booting.
On the client side, to set the system to boot through PXE, you need to change the boot sequence at the BIOS level: the PXE option must be first, with a higher priority than booting from external drives and local storage media.
Diagram of booting a system using PXE and the IPv6 protocol (source: Quarkslab)
PixieFail: Why Vulnerabilities in PXE Implementation Are Critical
The researchers of Quarkslab they discovered 9 serious vulnerabilities in Tianocore EDK II (Extensible Firmware Interface Development Kit II), the reference open source implementation used in UEFI. The result is that malicious users can interfere with the PXE boot process of systems used in the company to arrange for the loading of malicious code.
The various ones security flawscollectively baptized with the name PixieFail, have to do with support for IPv6 and a number of additional protocols that extend the attack surface. The gaps in question, if exploited, can allow DoS attacks (Denial of Service), the acquisition of confidential information, theremote code execution (RCE), DNS cache poisoning and hijacking (hijacking) of network sessions.
Examining the report of Quarkslabit emerges that the most critical vulnerabilities in absolute terms they are those identified by the identifiers CVE-2023-45230 and CVE-2023-45235. The first, in fact, concerns incorrect management of options Server ID (server identifier) of exceptionally long length within the DHCPv6 protocol. The DHCPv6 it is used in the context of PXE to obtain an IP address and other necessary network information during the boot process.
Generating an error buffer overflow occurs when the data received exceeds the size of the buffer that should contain it. In this case, “smart” exploitation of long Server ID options can allow the attacker to overwrite parts of memory leading to the execution of malicious code or system crashes.
The second flaw is similar, always having to do with the Server ID options and also leading to an error buffer overflow. In this case, the potentially “explosive” situation arises when a message is used Advertisewhen the server announces available network resources via PXE.
The root of security problems
Quarkslab indicates in NetworkPkg, part of the EDK II project, the root of the problem. This is the component responsible for implementing network boot support through the PXE protocol.
The vulnerabilities identified in NetworkPkg are in fact specifically linked to the network boot and they have to do with how EDK II implements PXE support, which is critical for booting systems in enterprise and data center environments.
Resolving the identified issues involves patching the source code of the PXE implementation (in this case, NetworkPkg) to mitigate vulnerabilities and protect the system from possible security threats.
The impact of vulnerabilities in PXE is broad
According to the experts of Quarkslabthe PixieFail vulnerability they affect a wide range of devices and vendor different. The researchers mention AMI, Phoenix, Insyde, ARM, Microsoft while the bulletin prepared and published by CERT/CC also refers to Intel.
Due to the complexity linked to the resolution of the vulnerabilities in question, the US CERT/CC has repeatedly postponed the disclosure of the existence of the various security problems in PXE, deciding to publish a notice only in mid-January 2024 (the flaws had already been known since August 2023).
At present, most of the patch are still in the preparation phase while Tianocore has provided fixes for some of the vulnerabilities.
In fact, as anticipated in the introduction, the entities most exposed to attack risks are those that manage a large number of systems. In particular, therefore, i provider Of services cloud.
You don’t need to set up a malicious server or get high-level privileges to launch an attack. All an attacker needs is access to the local network and the ability to send and receive packets, without needing any physical access. However, it is essential that the IPv6 support is enabled.
The oxen, however, have already left the stable: the researchers of Quarkslab they have in fact taken steps to publish this repository GitHub, il PoC code (Proof-of-Concept). It’s 9 script Python which allow you to target each of the vulnerabilities discovered in PXE.