The good old adage “never open attachments and documents from untrustworthy sources” is always relevant and helps protect you from a wide range of cyber attacks. There are situations, however, where you may need to open documents and unsafe attachments or potentially such. Danger zone is an application that creates a sandbox using Docker, runs LibreOffice there and converts any document to PDF format, using the open source office suite.
Users can use DangerZone for open different document formats, such as PDFs, images, Microsoft Office files, LibreOffice and content created with other programs. Even if the original document was potentially malicious and could damage your computer, DangerZone will transform into a PDF sure that it can be opened and read without risk.
When and why documents and PDF files can present risks
Documents and PDF files may present inherent risks due to the complexity of the formats and the possibility of possibly executing script incorporated. Although Microsoft has cracked down on VBA macros in Office documents, it is still possible to add scripts or code that can be activated automatically when the document is opened by the user.
The malicious scripts they are often designed to exploit vulnerabilities present in software used to open and view document contents. in document viewing software to perform malicious actions. If the user has not promptly applied the security patches released by various software manufacturers, opening a malicious document could be costly and lead to the execution of malicious code.
Some documents are designed to load external resourcessuch as images or scripts: attackers can thus know when their files are open on each system and arrange for the stealing of personal information.
How Dangerzone works and how it protects the user who opens unsafe documents and attachments
Available in versions for Windows, macOS and Linux, Dangerzone is designed to allowopening documents and attachments without risk. The operation of converting the original format to PDF allows, first of all, to neutralize anyone script, macro or malicious add-on. This simple trick allows you to generate a safe version of any file you want to open, benefiting from the isolated environment in which the “processing” of the source element is performed.
Pivoting on Docker, Dangerzone launches two container Linux. The first container converts the original document to PDF format. Subsequently, the PDF pages are processed as PNG images. The latter undergo further conversion and then transfer the output to a module OCR for optical character recognition.
When the user enables the OCR functionality, the content of each image is used to generate a Searchable PDF document: Each text element can be selected, copied elsewhere and used CTRL+F to locate a specific string.
If OCR is not enabled, then Dangerzone simply creates a normal PDF file: any texts present will not be selectable and possibly usable elsewhere. Dangerzone can convert to Secure PDFs items received in the following formats:
- PDF (.pdf)
- Microsoft Word (.docx, .doc)
- Microsoft Excel (.xlsx, .xls)
- Microsoft PowerPoint (.pptx, .ppt)
- ODF Text (.odt)
- ODF Spreadsheet (.ods)
- ODF Presentation (.odp)
- ODF Graphics (.odg)
- Hancom HWP (Hangul Word Processor) (.hwp, .hwpx)
- JPEG (.jpg, .jpeg)
- GIF (.gif)
- PNG (.png)
How to download and start using Dangerzone
The best way to use Dangerzone is to first install Docker. Subsequently you can refer to the download page to download and install the version intended for the operating system in use: Windows, macOS or Linux.
In the case of Microsoft and Apple systems, the developers of Dangerzone already offer pre-compiled binary fileswhich can be used to immediately run the program.
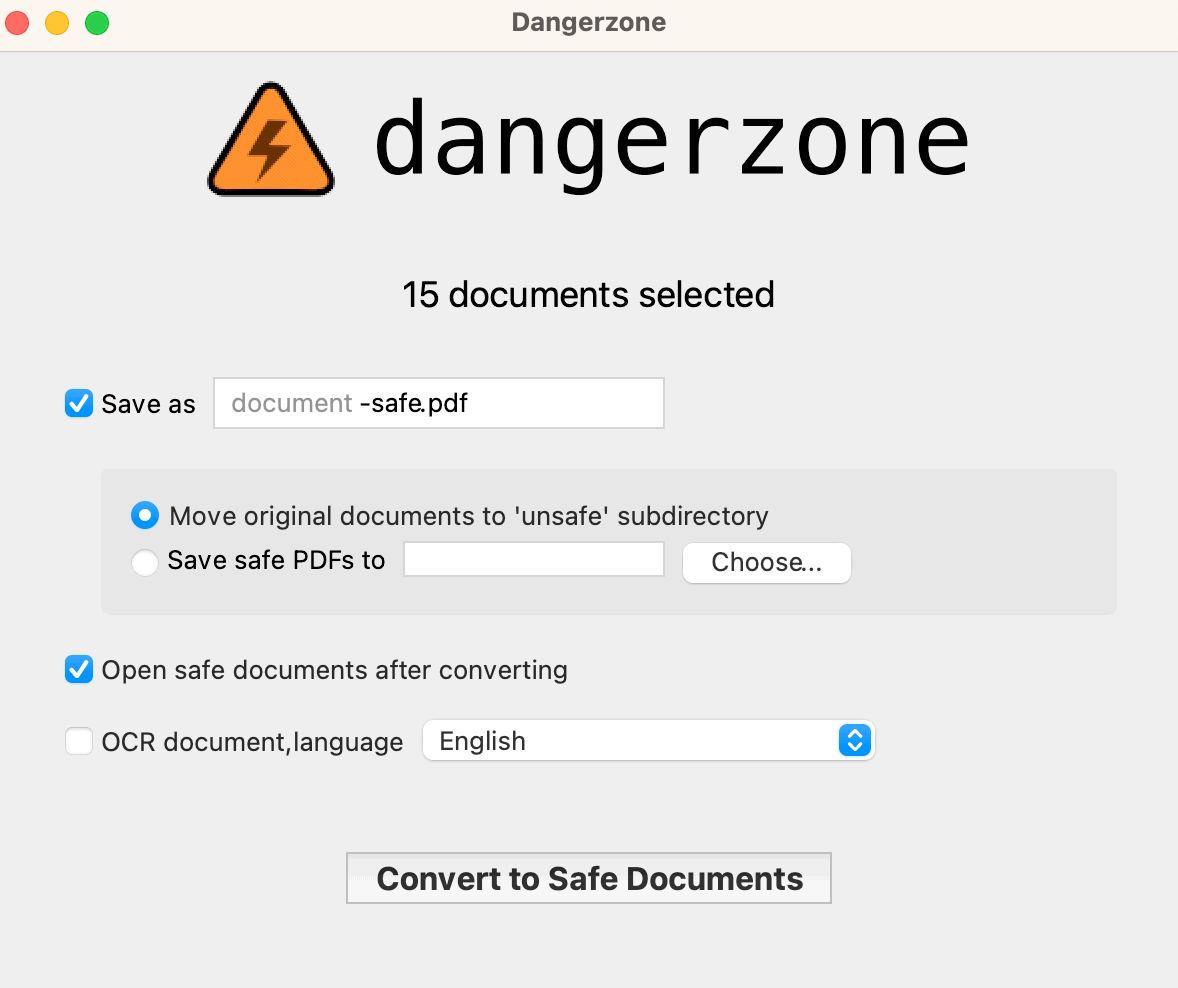
Once the Docker engine is running, Dangerzone allows you to select one or more documents to process and make safe. By default, files converted to PDF have the suffix added -safe. The original objects are instead stored in the folder unsafe and can then be removed. As lingua for the OCR engine, you can also choose Europen.
It must be said that the conversion procedure also makes the files more streamlined compared to the originals in the face of a contained loss in terms of quality.
Beware of residual risks
Although Dangerzone offers a protection effective, it is best to never let your guard down and not take anything for granted. In fact, no software is completely immune to potentials threats. Possible attackers could in fact develop malicious documents created to specifically target Dangerzone.
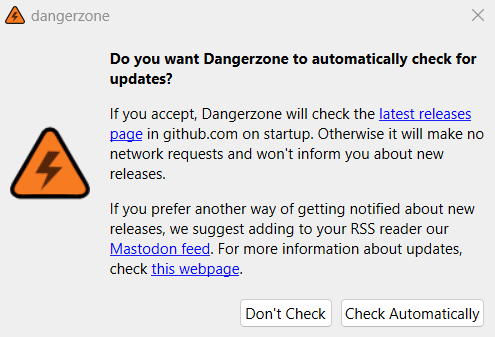
Furthermore, the software on which Dangerzone bases its operation, such as LibreOffice and Docker, may – themselves – suffer from some security vulnerabilities. The advice, obviously, is to install updates for Docker, always downloading and using the most recent release of Dangerzone (which in turn loads the most recent version of LibreOffice into the Docker container…). Upon startup, Dangerzone can be configured to periodically check for new versions of the program.
In general, as mentioned in the introduction, it is best to avoid opening potentially harmful documents and attachments because they come from unknown sources. If you are not in a position to do so, for example due to your activity or profession, Dangerzone represents an excellent solution. In any case, however, the computer used to open the PDF file generated with Dangerzone, should be precautionarily isolated compared to the rest of the local network.
Overall, Dangerzone is a software (open source, AGPLv3 license) that could prove decisive on multiple occasions. The flip side of the coin is a bit his heaviness: leaving aside the presence of Docker, the program installation file alone weighs 700-800 MB. It’s not exactly a feather.
Opening image credit: iStock.com – tsingha25