Do you remember the phenomenon of juice jacking presented in excessively alarmist tones by many authorities? These are USB ports set up by malicious users with the aim of damaging the downstream mobile device. In another article we asked ourselves whether juice jacking is really dangerous, highlighting how, to date, it is simply a laboratory experiment. In fact, there are no known cases of attacks “in the real world”.
Likewise, VoltSchemeran attack that appears to have highly destructive potential, is currently a proof-of-concept, an academic proof of the feasibility of an attack. It’s a long way from here to thinking that the problem identified could have large-scale effects. In any case, it is good to know what it is about without approaching the problem superficially.
VoltSchemer, beware of destructive wireless chargers
A team of researchers from the University of Florida and cybersecurity firm CertiK recently unveiled the attack VoltSchemer as a mechanism intended to cause physical damage to devices placed on them caricabatterie wirelesscausing potentially lethal consequences even for electronic products placed in the immediate vicinity.
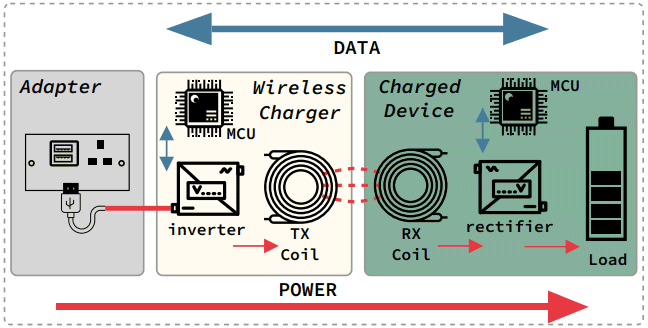
Wireless chargers use a technology called inductive charging to transfer energy from the power source to the device that needs to be charged without the use of cables. Both the wireless charger and the device to be charged contain induction coils: When the charger is connected to a power source, it generates a electromagnetic field through its coil. The magnetic coupling of the coils of the two devices induces an electric current, converted by a special internal circuit and used to recharge the battery.
Wireless charging devices integrate some safety features, such as battery control temperature and protection from overvoltagesto avoid overheating or damage to the device.
How the VoltSchemer attack works
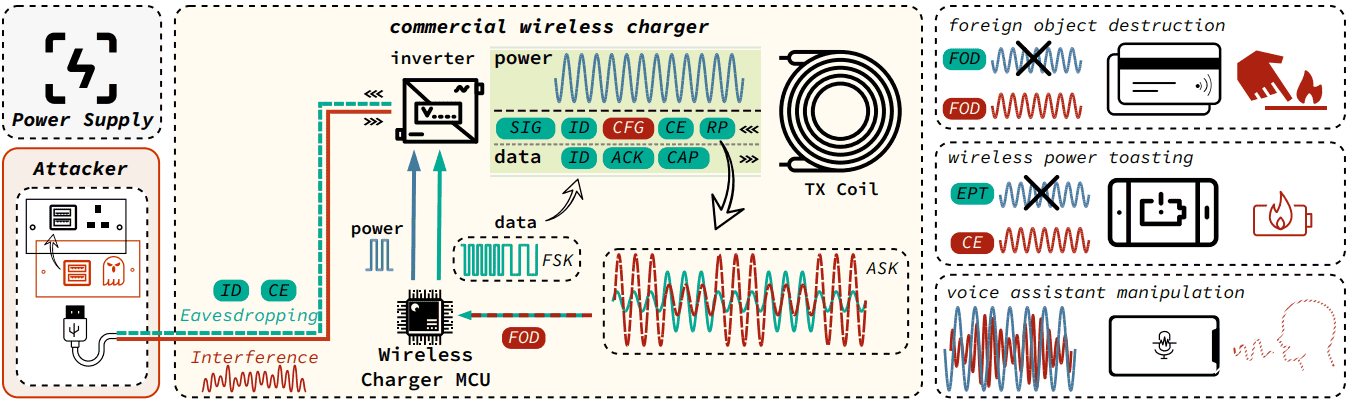
Using 9 wireless chargers, among the best-selling globally, as a “test bed”, researchers have detected some shortcomings that can lead to attacks VoltSchemer.
The principle consists in the use of electromagnetic interference which actually manipulate the behavior of the charger. Attackers can intervene on voltage supplied to the input of the battery charger and finely adjust its fluctuations to create an interference signal capable of altering the characteristics of the magnetic fields generated.
Voltage manipulation can be done through a device that stands between the power source and the wireless charger: this way no physical modifications are even required on the charging station.
The researchers claim that the interference signal interferes with the normal data exchange between the charging base and the smartphone, both of which are equipped with microcontrollori who oversee the process. This leads to distortion of the power signal and corruption of the transmitted data.
What threats does VoltSchemer introduce: exceeding security standards and injecting voice commands
Smartphones are designed to stop charging once the battery has reached its maximum capacity. In fact, they are able to communicate with the charging station to reduce or interrupt the energy supply. The noise introduced by VoltSchemer can interfere with these communications, keeping the power at maximum level and causing the overheating of the device placed on the charging base.
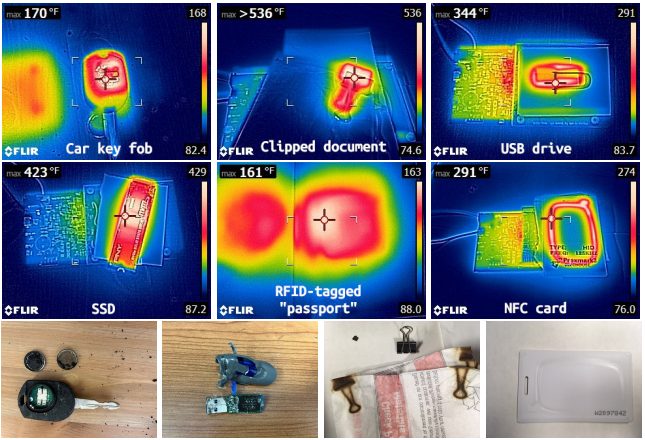
The second type of attack that the scheme VoltSchemer can introduce, results in the circumvention of the security mechanisms of the standard Qi in order to initiate the transfer of energy to unsupported and nearby objects. Think, for example, of car remote controls, USB sticks, devices equipped with RFID or NFC chips (access control, credit and debit cards,…), SSD drives and so on.
Even, leaving clips to collect sheets of paper near the wireless charger, taking advantage VoltSchemer the researchers managed to heat the paper clips up to temperature of 280 degrees, enough to make paper documents catch fire. Furthermore, electronic objects are certainly not designed to withstand these temperatures and could be seriously damaged.
The third type of attack described by the researchers consists in exploiting the noise generated by VoltSchemer per transmit inaudible voice commands to voice assistants Google Assistant on Android and Siri on iOS. The team demonstrated that it is possible to inject a series of voice commands through interference signals transmitted within the coverage radius of the charging station: you can thus initiate calls, open a website, launch an application and so on.
This type of aggression appears impracticable in a real scenario because it presupposes the command recording specific activation times for the victim’s terminal.
Be careful about the devices you connect
In all likelihood, exactly like the practice of juice jackingAlso VoltSchemer it is destined to remain a mere experiment. The most important aspect of the work published by the University of Florida and CertiK team is that wireless charger manufacturers have already taken action on reports to eliminate any risk of aggression from new models.
In general, however, wireless chargers of certain and safe origin should be used; Furthermore, you should always avoid the use of potentially harmful devices, disguised as legitimate accessories and distributed through various means such as promotional gifts, second-hand sales, or as replacements for supposedly defective products.
The images published in the article are taken from the document “Use Voltage Noise to Manipulate Your Wireless Charger“. The opening image is produced with Microsoft Bing Image Creator.