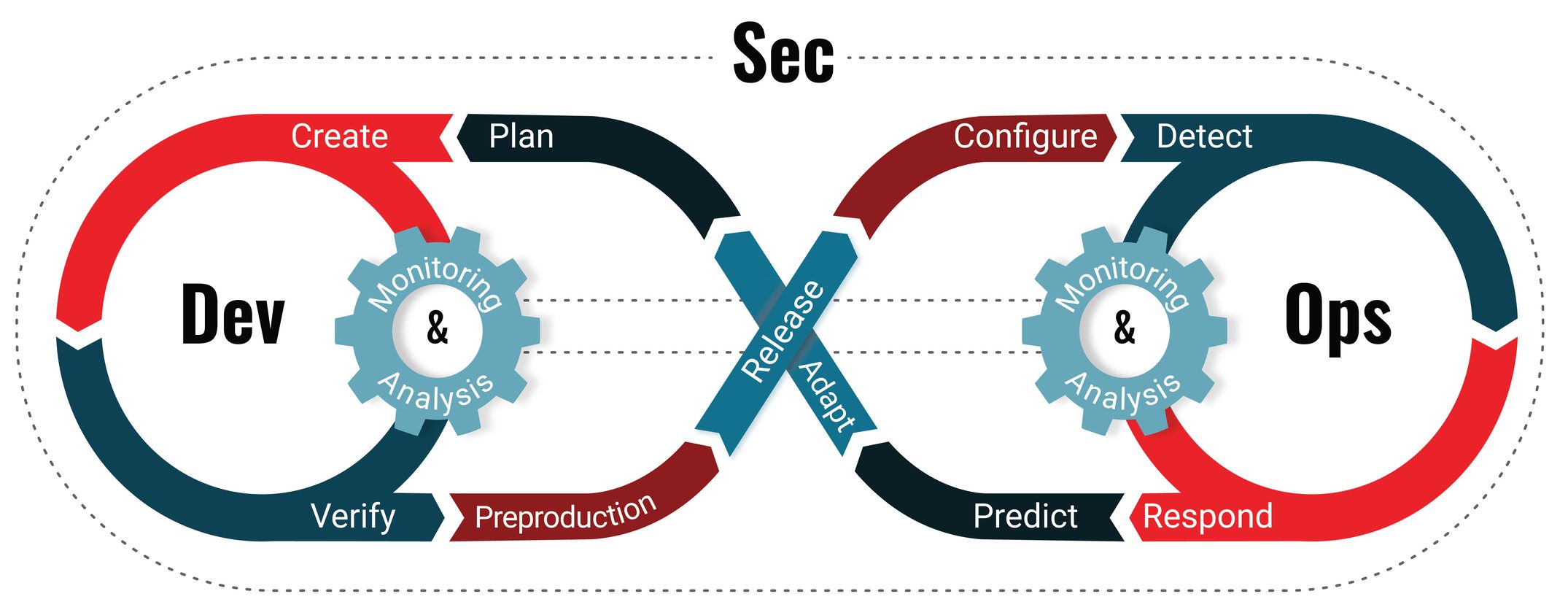
During the development of software and throughout its entire life cycle it is no longer possible to ignore the concept of safety informatica. DevSecOps it is a practice that integrates information security (Sec) in development processes (Dev) and in operations (Ops) within the organization. The main goal of DevSecOps is to focus on security aspects from the beginning of a program cycle, without ever treating them as a separate, subsequent activity. It is the evolution of the DevOps philosophy, which looks at the integration of automated tools and processes foranalyses static and dynamic of the codevulnerability scanning and access management.
The acceleration of cyber-oriented threats cloud and their effects, have made security a key priority for businesses, especially DevOps teams. Suffice it to say that according to the Global Threat Report 2023 by CrowdStrikethere was a 95% increase in cloud exploits in 2022.
It is critical to redefine the boundaries of security in application development
With the traditional approach DevOps, security was an issue that was addressed post-development. The situation, however, is finally changing. Now, developers who previously had to work on the coding until the last minute without having the material time to identify and fix vulnerabilitiesuse security features to ensure that code with security holes is not moved to production.
Raj Rajamani, Chief Product Officer CrowdStrike, notes that when security is considered at every stage of the production chain, developers can ensure issues are found and resolved early, reducing costs related to downstream fixes. The DevSecOps philosophy helps programmers address vulnerabilities early in the process app development.
By automating testing, remediation, and delivery, DevSecOps ensures greater software security, without slowing you down development cycles. The goal is to make security part of the workflow during software development, instead of having to deal with issues a runtimeadds Rajamani.
Five tips for developing better, more secure applications
The growth of applications cloud-native and the demand for faster application delivery – or one continuous integration/continuous delivery (CI/CD) – has led to a marked growth in the use of containers. This is why companies adopt the containerizationinstruments serverless and cloud-based services, which although on the one hand help to simplify and speed up software development, on the other introduce complex security problems. For this reason, CrowdStrike offers some advice key to it application development safe and efficient.
- Automate security reviews and tests. Every DevSecOps production chain, Rajamani notes, should use an automated, unified solution to have broad visibility into software-side issues detected. These are the activities that this tool should allow you to carry out:
- SAST: Static application security testing to identify at-risk source code before it is used.
- SCA: Software composition analysis for library vulnerability detection before production.
- CSA: Container scanning to detect weaknesses in operating system libraries and limit risks.
- IaC scanning: Scan infrastructure-as-code to detect infrastructure vulnerabilities
- ASPM: Application security management to detect fragilities and risks of the application once deployed.
- Integration with developer toolchains. Developers and security teams should focus on a single interface that integrates security and app development. The perfect integration with Jenkins , There , Bamboo , GitLab and other solutions in-cloudenables DevOps teams to respond quickly and resolve issues in a timely manner.
- Share security knowledge across teams. “DevSecOps is a technology-enabled journey, but it is a process that starts with people“, explains CrowdStike. The team should share information learned along with steps to mitigate threats once the issue is resolved. Some companies identify a safety reference figure who can coordinate the various individuals and make the team responsible.
- Measure the security level of the software. CrowdStrike also encourages you to identify critical points in your software development efforts and security risks. Tracking and measuring outcomes, such as time spent addressing vulnerabilities after code was injected, is also essential. The next step is to identify patterns in the types or causes of vulnerabilities introduced on the software side. These efforts help introduce a shared plan to integrate into the creation and production phases.
- “Shift right” e “shift left“. They are key concepts in DevSecOps development and refer to the temporal position of security activities in the software development lifecycle. “Shift left” refers to performing security tasks early in development: the goal is to identify and resolve vulnerabilities and security issues as early as possible.
The approach “Shift right” refers to performing security activities towards later phases of the software lifecycle, including the production phase and beyond. The goal is to focus on early detection of threats and security breaches in real operational environments and in the post-implementation phase.
While security and development were once separate, the lines are now decidedly more blurred. In the new perspective, corporate teams are brought together under a single umbrella, favoring business growth. “Security should not be an obstacle on the way to achieving business goals, or a cause of slowdown in software development“, conclude CrowdStrike. “Instead, it must enable you to achieve those goals safely and with minimal risk“.
Opening image credit: iStock.com – Visual Generation; image credit in the article: iStock.com – chokkicx