Is the VPN we use really effective? Does it protect our privacy? Let’s find out together with a series of tests.

When we use a VPN we want to achieve the utmost respect for the privacy of our devices and prevent our public IP address and our network traffic from being spied on by websites and the internet connection provider. Unfortunately, there are still many scenarios in which, even using a VPN, it is possible get some information about the hidden user, exploiting some weaknesses present on the operating system or web browser we are using at that precise moment.
To obtain the utmost respect for privacy and to browse truly anonymously, we recommend that you perform some simple tests to see if your VPN is workingprotecting any data that passes from the device to the chosen site.
If we find any vulnerabilities on our VPN connection we will also show you how to fix and prevent it from leaving our IP or connection data exposed in the future.
READ ALSO -> VPN comparison: which is the fastest and safest?
IP exposure test
A VPN hides our real public IP address, showing the sites we connect to a fictitious IP address (provided by the chosen VPN service).
To check if the IP is really disguised, simply log in to one of the many sites for check the public IP online, such as WhatsMyIPAddress. To carry out this test we first open the site without VPN and write down the public (real) IP address, then restart the browser in incognito mode, activate the VPN and repeat the test on the site.
If the VPN is working fine, a different (fictitious) public IP address, based on the server and the country we have chosen within the VPN service. Passing this test is very important, as it is the first purpose for which we install a VPN on our system (to disguise the personal IP address and obtain a fake IP address).
DNS server exposure test
When we open the web pages on the browser the requests are forwarded on server DNS, which act as huge telephone directories of web pages. When we use a VPN it is necessary that DNS requests are forwarded to the DNS servers of the chosen VPN serviceotherwise there will be an information leak (also called a DNS leak).
This loss of DNS information is very serious and significantly decreases privacy when using a VPN. The leaked DNS information allows our Internet provider or your chosen DNS provider (such as for example Google DNS) to discover which pages we visited under VPNalso identifying the real IP address.
To check that there are no leaks of DNS information, open a web browser without an active VPN connection, go to the DNS Leak Test page, press the button Extended Test and we await the results. In this scenario, the server provided by the telephone operator or one of the above should be visible as the DNS server server DNS alternativi freely configurable on PC or modem.
Now let’s repeat the DNS leak test by starting the VPN connection, opening the browser in incognito mode and repeating the test on the site indicated above; in this scenario the DNS server provided directly by the VPN service should be visible. Since it is difficult to understand the result, let’s also rely on the location and name of the service offered: if the result is profoundly different from that seen in the “unencrypted” test, we can rest assured, since there is no DNS leak.
If, on the other hand, we notice that the DNS server does not change under VPN the problem is serious: in these cases it is advisable to turn off the VPN, close the browser and try to change DNS settings on Windowsdisable any active proxies, change browser (choosing one without extensions) or change DNS inside the modem.
If the problem persists, we recommend that you change the VPN service immediately: The one we chose is not strong and secure enough to protect users from DNS leaks.
WebRTC exposure test
Another privacy hazard well hidden within browsers is richieste WebRTC. These requests are made by the protocollo WebRTC (used by many online streaming services and video conferencing services) to identify the starting IP address on the device along with the real public IP address, thus bypassing the IP verification obtained at the modem, router or network level .
This information leak is very serious and effectively renders the use of a VPN useless, as many services will know right away what real IP address is behind our VPN connection.
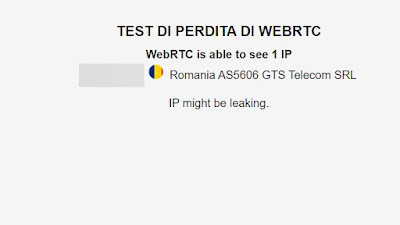
Fortunately, we can test this information leak by opening the VPNTesting site on our browser.
Also in this case let’s test without VPN connection first, so as to check if our real IP address is visible in WebRTC requests. After the first check we open the browser in incognito mode, activate the VPN connection, go to the site seen above and repeat the test; if everything works correctly the dummy IP address should also be visible in WebRTC requestsa clear sign that the VPN service chosen is very good and also protects against this information leak.
If instead our real IP address is visible in the WebRTC requests under VPNthe loss of information is active and it will expose our true identity on all sites that use WebRTC to function. This serious problem can be solved by switching browsers (using for example Mozilla Firefox), restarting the VPN or completely changing the VPN service used up to that point.
On Google Chrome we can also install extensions to prevent the leak of information on WebRTC; one of the best we can try is WebRTC Protect – Protect IP Leak, which blocks WebRTC-related IP requests, significantly increasing privacy.
Useful tips to increase the effectiveness of the VPN
If we really want to protect our privacy and obtain absolute anonymity when we surf the Internet, we should follow these simple tips, to be combined with a good premium VPN service:
- We use a browser without extensionsExtensions can expose your IP address or interfere with VPN operation. To be on the safe side, you should always use Mozilla Firefox without extensions as a browser for anonymous browsing.
- We always activate the incognito mode: whatever browser you choose, we always use incognito mode when we browse under VPN.
- We disable apps that are always connected: we avoid leaving active services always connected to the Internet (P2P client, TeamViewer, Zoom, online games or similar) while browsing anonymously. If these services are needed during the anonymous session, let’s activate them only after activating the VPN.
- We create a dedicated profile: your Windows suits create a local account dedicated only to anonymous browsing, so as not to interfere with the main Microsoft account.
- Use RAM cache on browsers: this trick will allow you to keep the browser cache on RAM memory onlyso as to cancel it simply by restarting or turning off the computer.
- Use Linux: le Linux distributions they are great for protecting privacy while browsing, but we will have to choose a Linux compatible VPN service.
By following these tips we will get a very high level of privacy and we will be able to browse in total anonymity using a VPN.
Conclusions
When we choose to protect our privacy with a VPN service we need to carry out tests to see if the chosen service is able to offer the promised level of privacy. With the tests seen in this guide we will immediately get the answers we were looking for, so as to be able to effectively protect privacy while browsing incognito.
Still on the subject of VPNs, we can read our guides on how configurare VPN su Router and how choose a secure VPN that does not spy on and does not share data.