All would-be “Sunday” hackers hope to get up one day and, with two clicks on the keyboard, easily enter the designated victim’s Facebook account, so they can see everything that is shared or messages sent to other friends.
All would-be “Sunday” hackers hope to get up one day and, with two clicks on the keyboard, easily enter the designated victim’s Facebook account, so they can see everything that is shared or messages sent to other friends.In addition to violating all laws on privacy and private property (in fact the account is a property, therefore violating it requires against very strict laws), entering someone else’s Facebook is not as simple as describing it around, it is necessary well-studied social engineering techniques, often tailored to the victim.
In this guide, we will describe you (without going into the specific tools used) the techniques still valid for entering another person’s Facebook and finally the methods we can use to defend our account against these threats.READ ALSO -> The basics of computer security
Techniques for entering another person’s Facebook
With the massive arrival of HTTPS and SSL on all Facebook pages the simple sniffing of packets exchanged on the network (perhaps in a public WiFi network) is no longer a viable way: the access data is encrypted from the PC to the server, we would sniff only unusable encrypted data.
But there are still some effective techniques that hackers can use to access other people’s Facebook accounts.
1) Keylogger
The keylogger is a malicious program or hardware device we study to record every key pressed on the keyboard, memorizing all the digits in an encrypted file that can be recovered by the hacker either via the Internet or by physically recovering the keylogger or the file it generates.
Hackers retrieve the Facebook email and password simply by reading our keystrokes.
Software keyloggers are actually viruses, so many antiviruses react to it and protect us from the threat of interception by blocking the execution of the program.
The hardware keyloggers are much more sophisticated and difficult to intercept: these are nothing more than small devices (PS / 2 or USB) that are interposed between the connection of the wired keyboard and the PC port, intercepting the data during transit.
All the keys pressed are stored in the internal memory of the hardware keylogger, ready to be spied on.
The victim’s PC will not notice anything, as will the antivirus (which cannot intercept a hardware keylogger).
At the end of the espionage work, the hacker will only have to physically recover the keylogger and download the data contained therein to enter another person’s Facebook with ease.
READ ALSO -> Best Anti-keyloggers for free against malware that spies on your computer
2) phishing
Another technique used to steal other people’s Facebook accounts is to send phishing emails to the victim.
These trap emails will ask the victim to re-enter the Facebook access data into a malicious page created ad hoc (often quite similar to the original Facebook page) due to login problems or other types of problems, often cited to create panic in the victim (“your Facebook account will be deleted”, “Facebook will become a fee if you do not enter data immediately”, etc.).
Using sophisticated social engineering techniques, the frightened user will insert his Facebook credentials without too much trouble into the page created by the hacker, effectively giving away his access data.
The danger of these emails can be difficult to understand, especially for novice users with the world of computing and the Internet.
READ ALSO -> Recognize false, fraudulent e-mail not authentic
3) Theft devices
The most direct and dangerous way to enter another’s Facebook is to steal a victim’s PC or smartphone, with all the risks involved.
Compared to the previous methods (which allow you to go unnoticed even if the threat is discovered) this is what jeopardizes both the security of the hacker and his safety since it is not known how the victim will react to theft.
Being a hacker does not mean automatically being good pickpockets!
READ ALSO -> Anti-theft app for Android to control and block the phone from a distance
4) Man-in-the-Middle attack
One way to access someone else’s Facebook is to make a difficult Man-in-the-Middle attack, where the hacker replaces one of the servers used for the connection and thus manages to capture the access data via a page. Fake Facebook, even if completely similar to the original.
Since the pages are encrypted and certified, it could be very difficult for the hacker to carry out this type of attack, since he will have to deceive the modern security systems of the browser (which signals when a page presents unauthenticated or secure certificates).
But laziness and the inability to identify dangers could lead many users to blindly trust what they see on the monitor, unknowingly providing all the access data to the “listening” hacker.
If this type of attack succeeds, it is very difficult to trace the author of the attack just as it is practically impossible to understand whether we are still under attack or not!
5) Device cloning
This is definitely the most advanced technique, used by high-level hackers and very difficult to apply since in many cases the program will have to be configured manually (so excellent programming knowledge is required in all currently known languages).
The hacker approaches the unaware victim and, within a certain range, starts an app on the smartphone that can “clone” all the apps and data contained in the victim’s smartphone.
Compared to the film cloning that we see in the TV series or in the movies (two-three seconds and so on!) This copying process requires more hours, since it uses NFC, WiFi Direct and Bluetooth to perform the cloning and, in case of a lot of data to copy, a large amount of time may be required.
The two phones must remain close enough to carry out the copy process, so the hacker will need a situation in which we abandon the smartphone in a precise place for a long time: while we sleep, while we are in the shower, while we are in class at the university (maybe we left the smartphone to the professor’s chair to record the audio of the 2-hour lesson …).
At the end of the copying process, the hacker’s smartphone will be completely identical (software side) to the victim’s smartphone, so he can access the Facebook app and any other personal information without problems.
The cloning apps are difficult to use and to program, but smartphone devices that are ready to use for cloning any modern smartphone are also commercially available (on Darknet), although they still require extraordinary capabilities to be prepared for copying.
How to defend your Facebook account from hackers
From the first part of the guide, we realized that there are still many methods to enter another person’s Facebook, so we will have to adopt strategies to defend ourselves adequately.
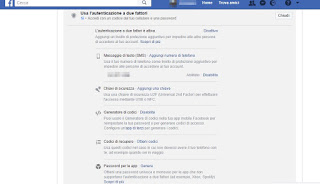
1) Enable two-factor authentication
A first defense system against hackers is offered to us by Facebook itself: when we log in with our credentials we will have to enter a code sent via SMS or via a dedicated app to confirm our identity.
We can activate this security system (effective against hardware, software, MITM and phishing keyloggers) by opening our Facebook account, by clicking at the top right on the arrow-shaped menu, clicking Settings -> Protection and access and finally enable the voice Use two-factor authentication.
We choose which method to use for authentication between all those available, so as to have more than one method to securely access your account.
READ ALSO -> Sites/apps where to activate two-step password verification
2) Install a good antivirus on PC
Choosing a good antivirus will allow you to block all keyloggers and malicious links that can be sent via phishing emails.
A good free antivirus that we recommend to use to protect the whole PC is Kaspersky Free, available here -> Kaspersky Free.
Already in its free version, it is able to effectively stop all types of threats for PCs with Windows, while also providing protection against malicious links (via the dedicated extension).
3) Use a VPN
To avoid Man-in-the-Middle attacks it can be effective to mask every trace of our Internet connection using a VPN connection.
With the VPN all our traffic will be further encrypted and our connection will be anonymous (even the IP will be masked), considerably increasing security while browsing.
Among the free VPNs, we mention Avira Phantom VPN, which can be downloaded for free here -> Avira Phantom VPN.
We start the program when we want to increase network security or when we connect to networks of strangers or public networks, so as to avoid any kind of attack mediated through hacker tools.
READ ALSO -> Better services and free VPN programs for safe and free browsing
4) Protect your smartphone
The most dangerous and effective attacks can be carried out against our smartphone, so we recommend concentrating on it in order to better protect our Facebook account.
In addition to common sense (we avoid leaving the smartphone unattended for more than 15 minutes), we can install an anti-theft device and an antivirus, to be activated when we are forced to leave our smartphone unattended.
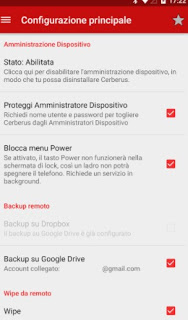
A good burglar alarm for smartphones is the Cerberus burglar alarm, which we can download here -> Cerberus burglar alarm.
With this app installed we will no longer have to fear the theft of the smartphone.
We will be able to recover the lost device position, take photos and videos of the hacker without being aware of it, start an audible alarm, make remote settings via SMS and prevent switching off or formatting (at least on some devices).
We recommend using the Kaspersky Mobile Antivirus app as an antivirus and app blocker: AppLock & Web Security, downloadable from here -> Kaspersky Mobile Antivirus: AppLock & Web Security.
This complete suite protects against attacks of any kind and also offers an App Lock, a call and SMS filter and a very effective anti-theft system to immediately find your smartphone.